Mutual Authentication (mTLS) Beta
You can use our Mutual Authentication mode, which incorporates Mutual TLS (mTLS), to enhance the security of your Salesforce Fivetran connector. This added layer of security ensures a 2-way authentication process, where both Salesforce and Fivetran verify each other’s identities before any data exchange occurs. During the connection setup, both Salesforce and Fivetran exchange and validate each other's certificates, ensuring a secure and trusted communication channel.
Setup instructions
Enable mutual authentication in your Salesforce account
Follow the instructions provided in this Salesforce guide to enable mutual authentication for your Salesforce account.
NOTE: Once mutual authentication is enabled for a user profile, that user cannot log in to their Salesforce account via UI.
Generate and upload CA-signed certificate
Perform the following steps to generate and upload a Certificate Authority-signed (CA-signed) certificate and set up mutual authentication for your Salesforce account:
Generate Salesforce certificate and certificate signing request
To generate a Salesforce certificate and a Certificate Signing Request (CSR), do one of the following:
- Follow steps 1 through 9 provided in the Salesforce documentation.
- Use a command-line utility, such as OpenSSL.
IMPORTANT:
- The Common Name (CN) of the certificate must be a trusted domain that you own. For example,
https://www.mycompany.com.- Use a public Certificate Authority (CA) (for example, DigiCert) that is trusted by Salesforce to sign the certificate. For the list of CAs trusted by Salesforce, see the Salesforce website.
- If you use a command-line utility to generate the client certificate and CSR, you may be prompted to set a passphrase for the private key. Do not specify a passphrase, as it is not supported.
- Self-signed certificates are not supported and will be invalidated by the Salesforce server.
Prepare certificate and private key files
Verify whether the signed certificate bundle contains the root and intermediate certificates.
Verify whether the certificate metadata lists a public CA as the issuer.
TIP: You can inspect the certificate metadata using tools such as SSL Shopper’s Certificate Decoder or OpenSSL commands.
Combine the client, intermediate, and root certificates into a single file, ensuring the following order:
i. Client certificate (top)
ii. Intermediate certificate (middle)
iii. Root certificate (bottom)
Separate each certificate with
BEGIN CERTIFICATEandEND CERTIFICATEblocks.Save this file in
.pemformat.Save the private key in a separate file in
.keyformat.
Upload certificate file
Follow the instructions provided in the Salesforce documentation to upload the mutual authentication certificate. When you are asked to upload the file, upload the same .pem file that you uploaded to Fivetran.
Configure connected app
To use mTLS with OAuth2.0 client-credential flow, you need to configure a new connected app in your Salesforce account. To do this, perform the following steps:
Follow the instructions provided in this Salesforce document to configure a connected app for the client-credential flow. Assign the client credential flow to the user that you have enabled the mutual authentication profile for.
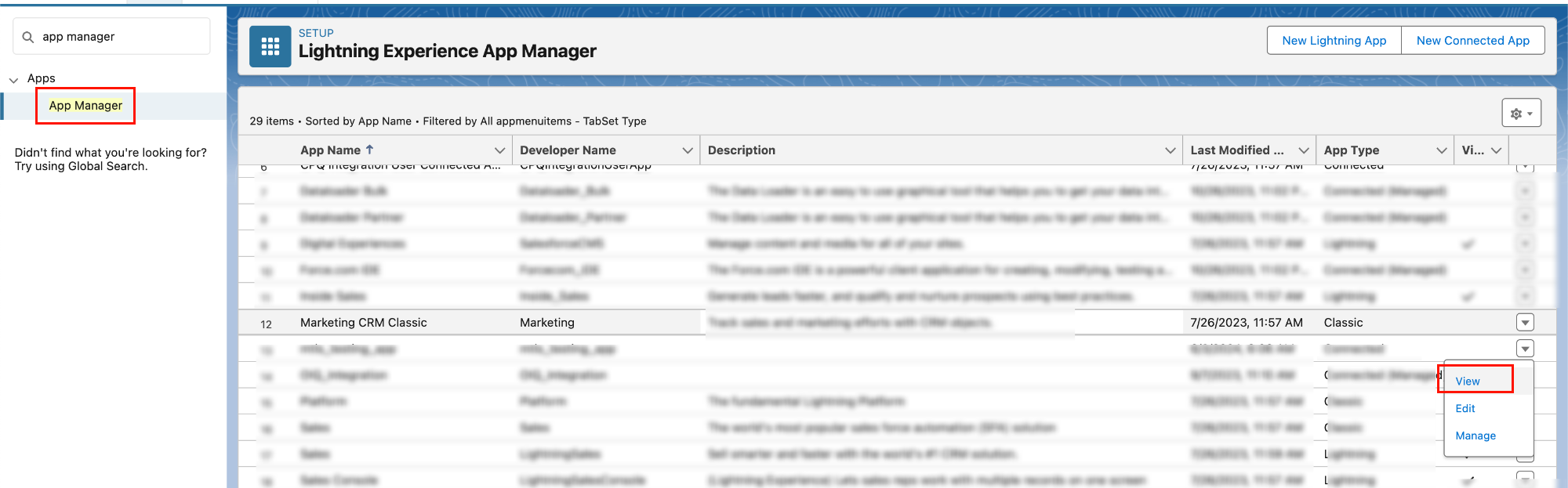
After creating the app, go to Setup > App Manager.
Select the configured connected app and click View.
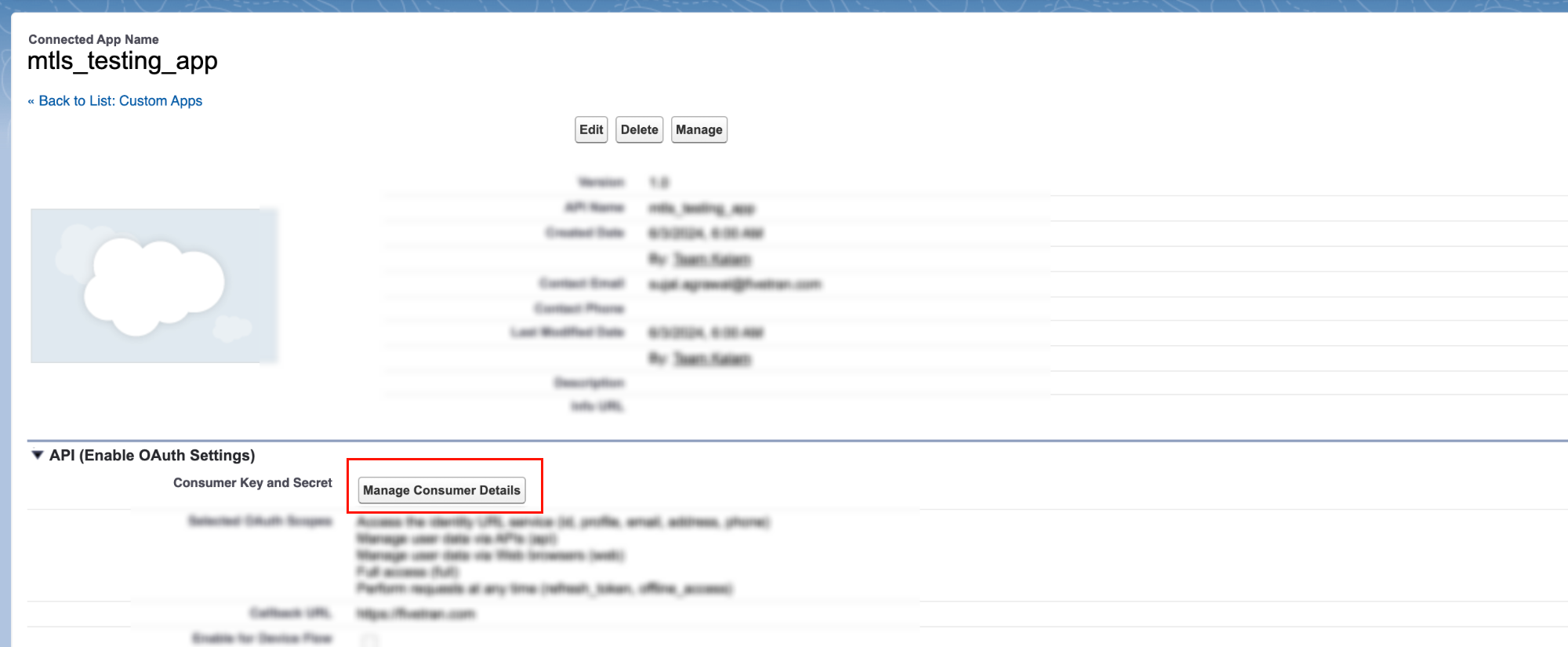
Click Manage Consumer Details. Make a note of the consumer key and secret.
Find your My Domain URL
Find the My Domain URL associated with your Salesforce account. For example, https://MyDomainName.my.salesforce.com or https://MyDomainName--SandboxName.my.salesforce.com for Salesforce or Salesforce sandbox instances, respectively.
Finish Fivetran configuration
- Go back to the Fivetran Salesforce connector setup form.
- In the connector setup form, select mTLS as the Authentication Method.
- Complete the connector setup.