Role-Based Access Controls
Role-Based Access Controls (RBAC) let you manage the set of permissions an individual user has.
RBAC provides peace of mind, ensuring only those with appropriate permissions can access sensitive user information or take potentially destructive actions with Census Syncs or Census configuration.
Organization Administrators
Members of a Census organization may be promoted to Administrators, which will give them Owner permissions in all Workspaces and the ability to manage billing, and Organization level settings.
When you migrate your Census account to Fivetran, all Census Admins who are not also Fivetran Account Administrators are downgraded to Owners for security reasons. A Fivetran Administrator can restore their permissions after the migration.
Users who are not an admin are simply Members of the organization. Members must be added to each workspace individually.
Workspaces and Roles
Each member of a workspace has a role within each (and their roles can vary across workspaces).
- Owner – This gives access to everything within the workspace, including managing warehouse & destination connections, API keys, and adding/removing users. Organization Admins have all the same permissions as Owners within a workspace.
- Editor – This role allows users to create datasets, segments, and syncs, but does not give the ability to create or manage connections
- Operator – The Operator Role is a special role within Census. It fits between the Editor and Viewer permissions, allowing members with this role to primarily work with Segments. Operators are able to create and edit segments, as well as manage syncing datasets and segments. They won't be able create new datasets, or modify any existing connections details.
- Viewer - The read-only viewer on Census. They can view syncs and segments, and approved models, but cannot modify or take any action within Census.
| Action | Viewer | Operator | Editor | Owner |
|---|---|---|---|---|
| View Warehouse Connections | ✅ | ✅ | ✅ | |
| Test Warehouse Connections | ✅ | ✅ | ✅ | ✅ |
| Create & Manage Warehouse Connections | ✅ | |||
| Create & Manage dbt / Looker Connections | ✅ | |||
| Create & Manage Org-level Fivetran & dbt Cloud Integrations | ✅ | |||
| View Destination Connections | ✅ | ✅ | ✅ | |
| Create Destination Connections | ✅ | |||
| Manage Destination Connections | ✅ | |||
| Create custom objects, audiences, and tables in destination | ✅ | ✅ | ✅ | |
| Preview Sample for Datasets | ✅ | ✅ | ✅ | ✅ |
| Query Models | ✅ | ✅ | ✅ | ✅ |
| Create & Edit Datasets | ✅ | ✅ | ||
| Create & Edit Segments | ✅ | ✅ | ✅ | |
| Create & Modify Exclusion Lists | ✅ | |||
| View Syncs | ✅ | ✅ | ✅ | ✅ |
| Create, Edit & Run Syncs on Segments & Datasets* | ✅ | ✅ | ✅ | |
| Create, Edit & Run Syncs on Datasets, Tables & Views | ✅ | ✅ | ||
| Invite New Users | ✅ | ✅ | ||
| Manage Member Roles | ✅ | ✅ | ||
| Remove Members from Workspaces | ✅ | |||
| Create, Manage, Delete Workspaces | ✅ | |||
| Create & Manage API Keys | ✅ |
Custom Roles
You can also create custom roles by combining the required set of fine-grained permissions into a role that is then assignable to users in any workspace. Custom roles give you the ability to create narrow roles for specific use cases such as connection administration or data definition.
Custom Roles are available on Enterprise plans only.
Custom Roles do not yet give access to Organization-level management permissions such as billing managements.
To create a new custom role,
- Click on the Workspaces selector at the top of the left navigation and click Organization Home.
- Click on the Roles tab.
- Click + New Role
- Give your New Role a name.
- You may also optionally pick an existing role to use as a starting point. Note that once your new role is created, there's no lasting association with this role, this is purely to save yourself some clicks setting up your new role.
- Select the combination of permissions your new role needs and then click Save.
You can also manage the permissions of existing roles here. Modifying the permissions of an existing will take effect immediately on any user assigned to that role (though they may need to refresh their browser session to see it in the Census UI, it will be enforced immediately if they try to take a now blocked action).
Available Permissions
Custom roles are a collection of permissions granted to the user within that workspace. They are organized as follows:
- Subject - The type of resource (or group of related resources) that the set of permissions apply to, such as a connection, sync or dataset.
- Permission - The specific allowed type of action that can be taken on the subject.
| Subject | Permissions | Description |
|---|---|---|
| API Token | Read, Manage | Most Census API endpoints today are accessed via a shared API token defined for each Workspace. |
| Workspace | Update, Read Members, Remove User | Manage the configuration associated with the workspace, including listing and removing members. |
| Workspace Member | Manage [Role] | Specifically grants the ability to invite, assign, or revoke a particular role for members in the workspace. The Custom Role version applies to all custom roles so should only be used for admin roles. |
| Connections | Test, Create, Update, or Destroy | Permissions that apply to the creation and management of both source and destination connections. Note: All members of the workspace will be able to see the existence of any connections regardless of permissions. |
| Segment | Read, Create, Update, Destroy | Permissions related to listing, creating, updating, and destroying Segments. |
| Segment Priority Lists | Read, Create, Update, Destroy | Permissions scoped specifically to the Segment Priority List functionality used to manage overlapping segments. |
| Segment Exclusion Lists | Read, Create, Update, Destroy | Similarly scoped permissions for managing exclusion lists set up within Audience Hub. |
| Cohorts | Read, Create, Update, Destroy | Similarly scoped permissions for managing experiments created on top of Audience Hub segments |
| Smart Columns | Read, Create, Update, Destroy | Permissions controlling access to smart columns, including computed columns, formula columns, and AI columns |
| Metrics | Read, Create, Update, Destroy | Scoped permissions for setting up performance metrics used to measure segment performance in Audience Hub. |
| Sync Configuration | Read, Create, Update, Destroy | Standard operations for creating and managing syncs |
| Read, Create, Update, Destroy from dataset or segment | Scoped versions of the above operations limiting sync creation to only existing datasets or segments. Used by the built-in Operator role. | |
| Run, Full Sync | Grants the ability to manually trigger a sync or full sync | |
| Access Sync Tracking | Download and search detailed sync tracking logs | |
| Manage Subscriptions | Control which users will be alerted if a sync encounters an issue. | |
| Project | Read, Create, Update, Destroy | Standard operations for managing Dataset project/repositories. |
| Dataset | Read, Create, Update, Destroy | Standard operations for creating and editing datasets, such as SQL queries. |
| Datadog Integration | Read, Create, Update, Destroy | Standard operations for enabling and managing the datadog integration for each workspace |
| Navigation | Visit Syncs, Segments, Datasets, Connections, Settings | Controls access to the various navigation sections of Census. These permission primarily controls navigation itself, not access to underlying resources, which are managed by other permissions. |
Disabling Data Previews
Census provides sample data when working with models, segments, and syncs to help users understand their data sets, as well as what's being synced. Some organizations may prefer to restrict the ability to preview data to specific tools.
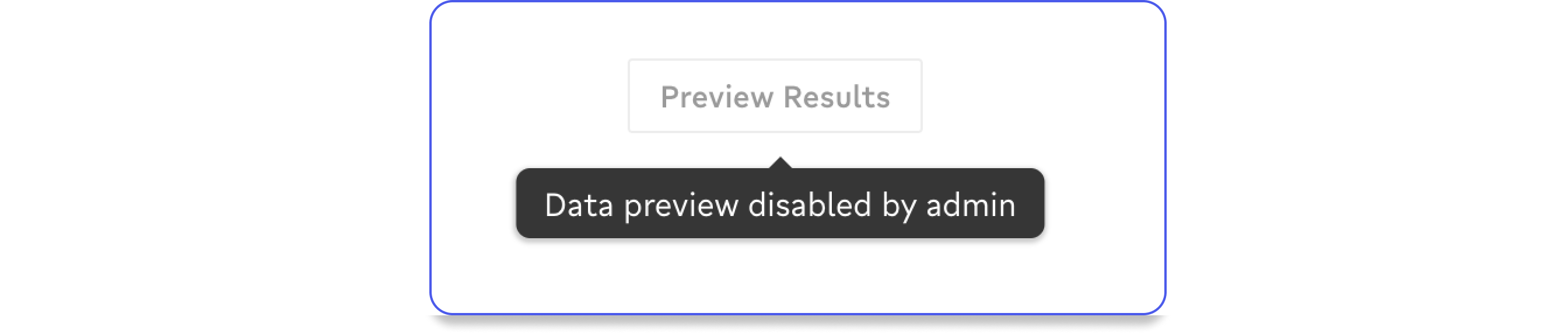
In this case, you can choose to disable the ability to preview data in Census on a per workspace basis. To disable data previews in Census, reach out to your success manager or open a ticket with Fivetran Support.