AWS Customer-Managed Keys Setup Guide
Follow our setup guide to configure AWS customer-managed keys.
Prerequisites
To set up AWS customer-managed keys for your Fivetran account, you need:
- A Business Critical Fivetran account
- An AWS account.
Setup instructions
Create AWS key
Log into your AWS console.
In the Security, Identity, & Compliance section, go to Key Management Service.
Click Create key.
In the Key type section, select Symmetric.
In the Advanced options section, select Multi-Region key. Click Next.
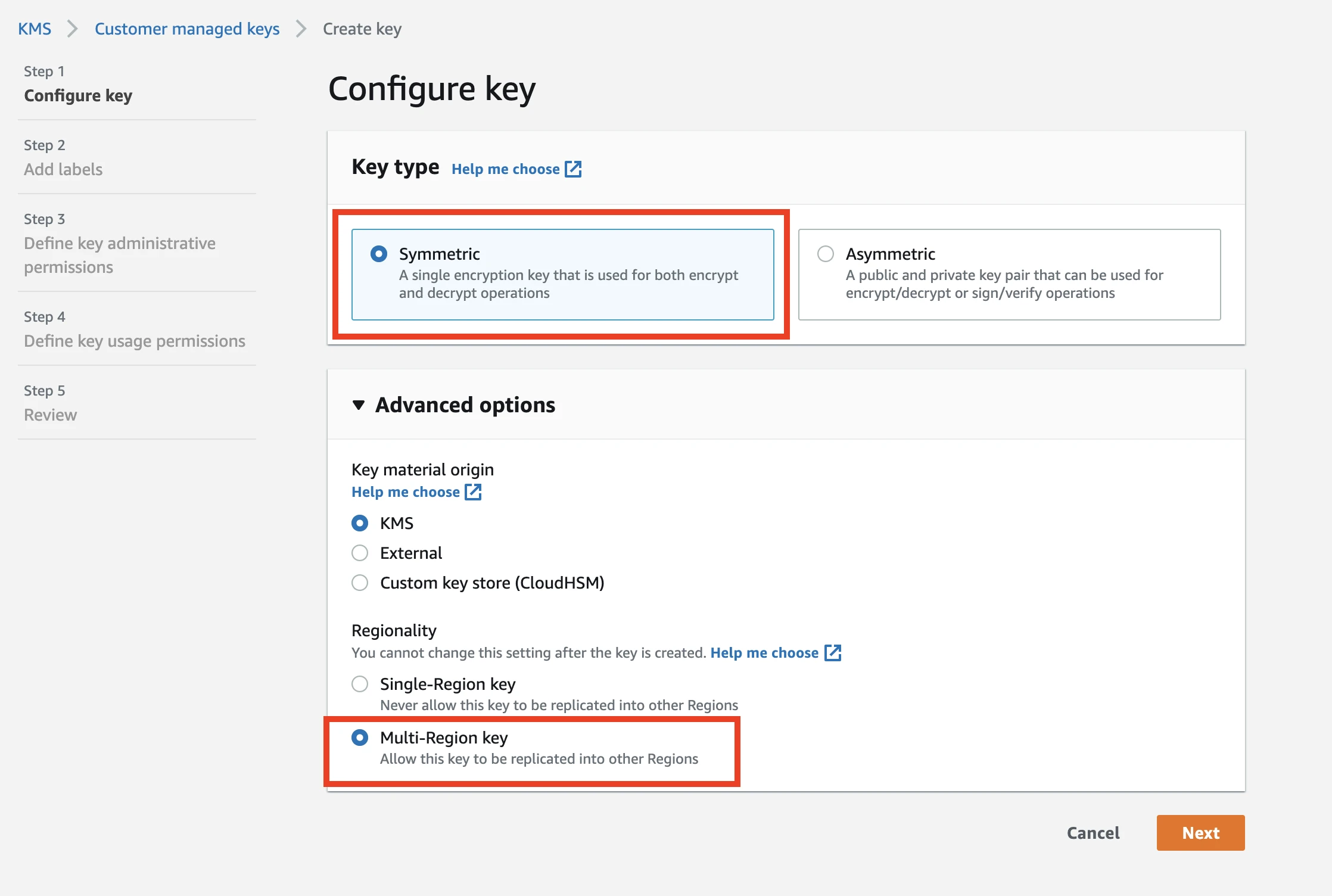
Enter an alias. (Optional) Enter a description. Click Next.
Choose the users and roles to administer the key. Click Next.
Review the key policy and click Finish.
Click on the newly-created key. Make a note of the key's ARN. You will need it later to configure Fivetran.
Create IAM policy
- Go to your IAM console.
- In the Access Management section, go to Policies.
- Click Create Policy.
- On the Create policy page, go to the JSON tab.
- Copy the following policy into the JSON editor. Replace
{your key ARN}with the key ARN you found in Step 1. Make sure you use the complete ARN. The key ARN has the following format:arn:aws:kms:<region>:<account_id>:key/<key_id>. An example of a key ARN:arn:aws:kms:us-east-1:000000000000:key/mrk-00000000000000000000000000000000.{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "kms:Decrypt", "kms:Encrypt", "kms:GenerateDataKey", "kms:ReEncryptTo", "kms:GenerateDataKeyWithoutPlaintext", "kms:DescribeKey", "kms:ReEncryptFrom" ], "Resource": "{your key ARN}" } ] } - Click Next: Tags. (Optional) Add tags.
- Click Next: Review.
- Enter a memorable policy name (for example, “Fivetran-KMS-Access”).
- Click Create Policy.
Create IAM role
- Return to the IAM console.
- In the Access Management section, go to Roles.
- Click Create role.
- Select Another AWS Account as the role type.
- In the Account ID field, enter Fivetran’s account ID,
834469178297. - Select the Require External ID checkbox. In the External ID field, enter your Fivetran account ID from the dashboard.
- Click Next: Permissions.
- Select the IAM policy you created in Step 2.
- Click Next: Tags and (optional) add tags.
- Click Next: Review.
- Enter a role name.
- Click Create role.
- On the Roles page, select the Fivetran role you just created.
- Copy the role’s ARN.
Finish Fivetran configuration
- In the Fivetran dashboard, go to Account Settings > General > Customer-Managed Keys Configuration.
- Click Add Key.
- Select AWS Key Management Service.
- Enter the Key ARN you obtained from Step 1.
- Enter the Role ARN you obtained from Step 3.
- Click Submit.