Single Sign-On Using Microsoft Entra ID
Follow our guide to set up single sign-on (SSO) into Fivetran using the Fivetran Microsoft Entra ID (formerly Azure Active Directory) gallery application.
Prerequisites
To use Microsoft Entra ID SSO with Fivetran, you need Azure and Fivetran accounts.
In Azure
Add and configure the Fivetran application
Log in to your Azure account and go to the Microsoft Entra ID service.

In the left menu, select Enterprise Applications.
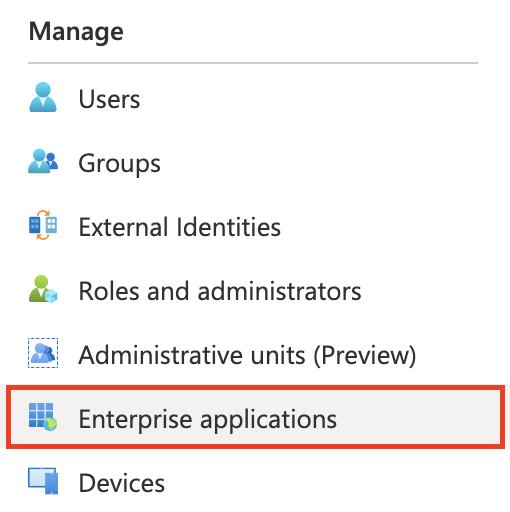
Click New Application.
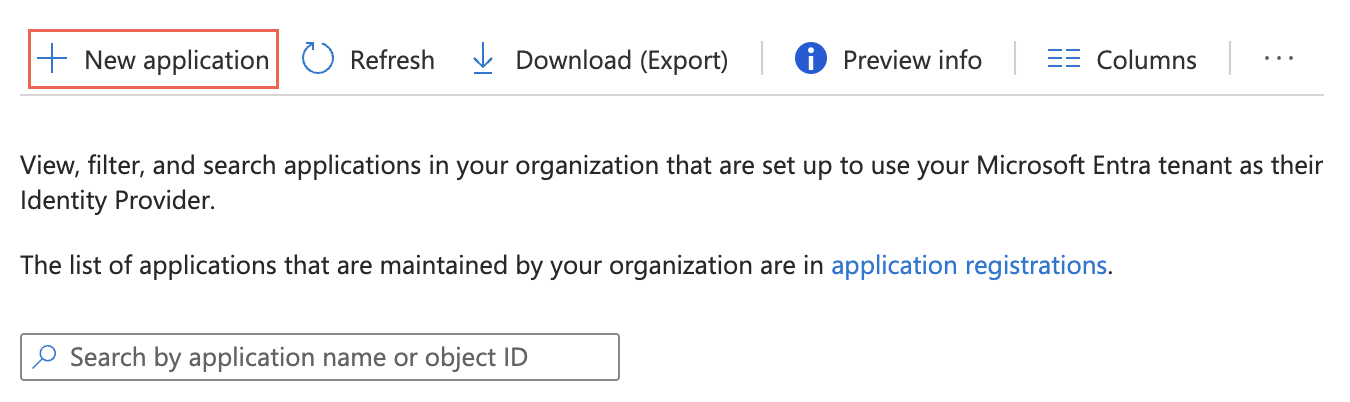
Enter Fivetran in the search box.
Select the Fivetran application.
Click Create.
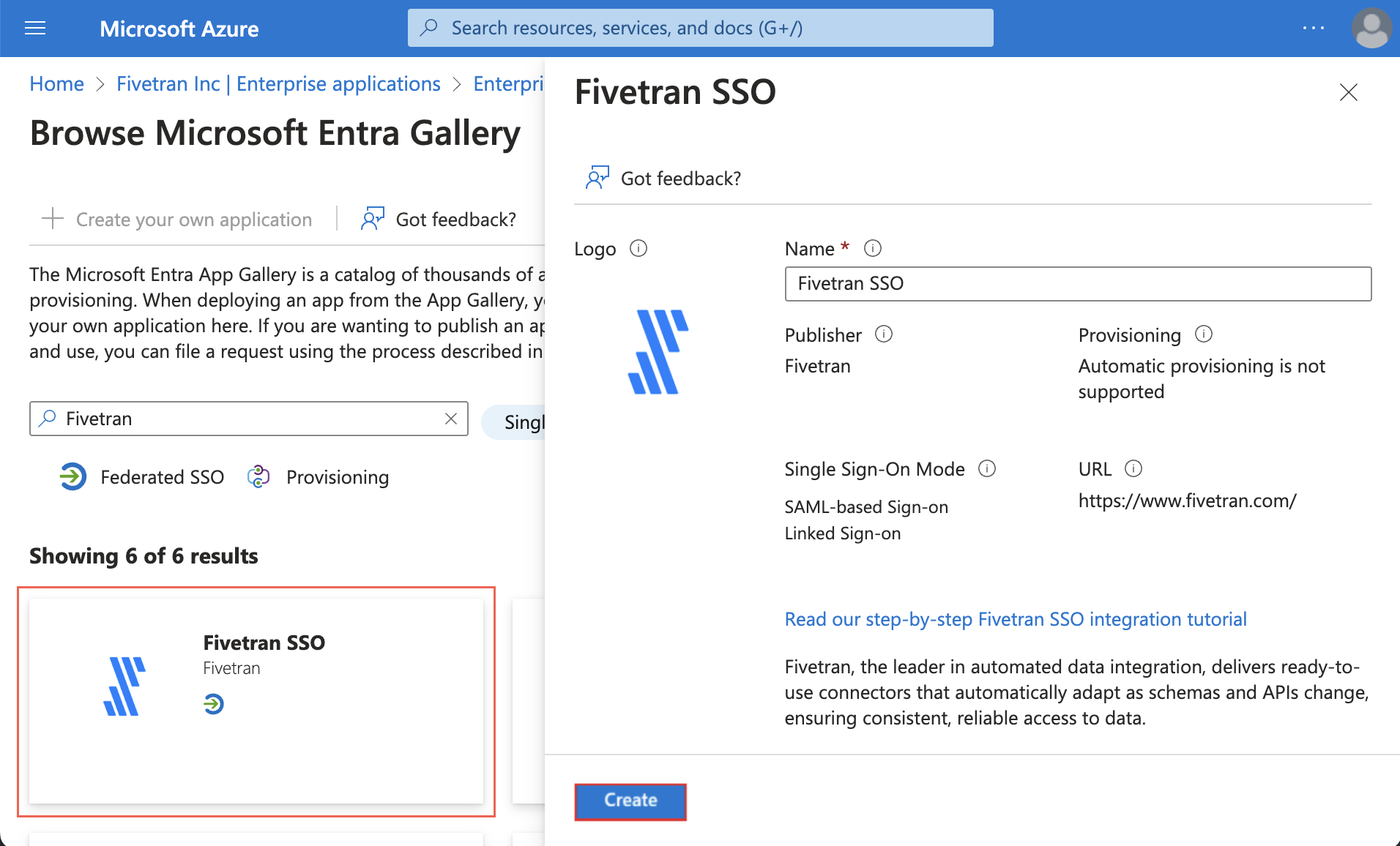
In the Getting Started section, select Set up single sign on.

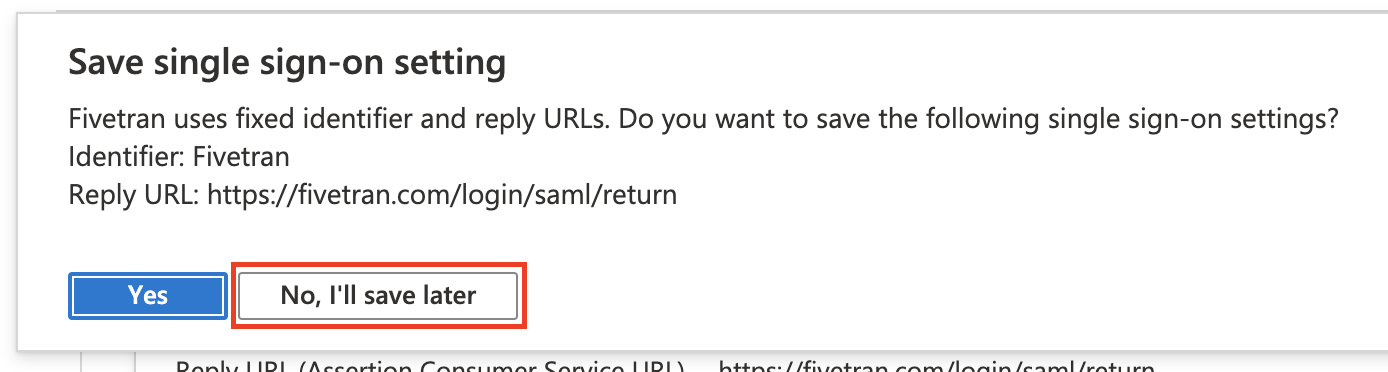
Under Select a single sign-on method, select SAML.

In the Save single sign-on modal, click No, I'll save later.
In the Basic SAML Configuration box, click Edit.
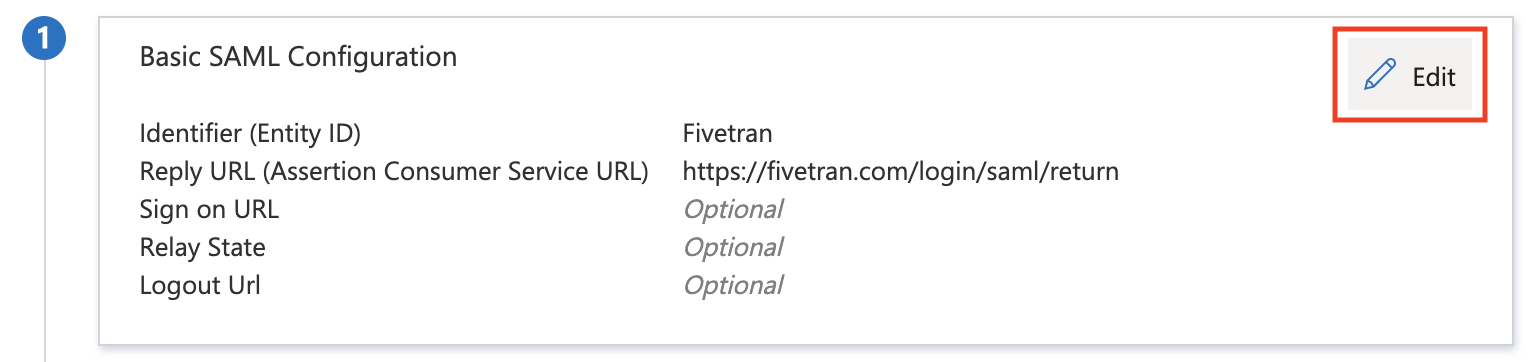
Click Save. The settings are pre-configured.
Click Edit in the Attributes & Claims section.
Click + Add new claim.
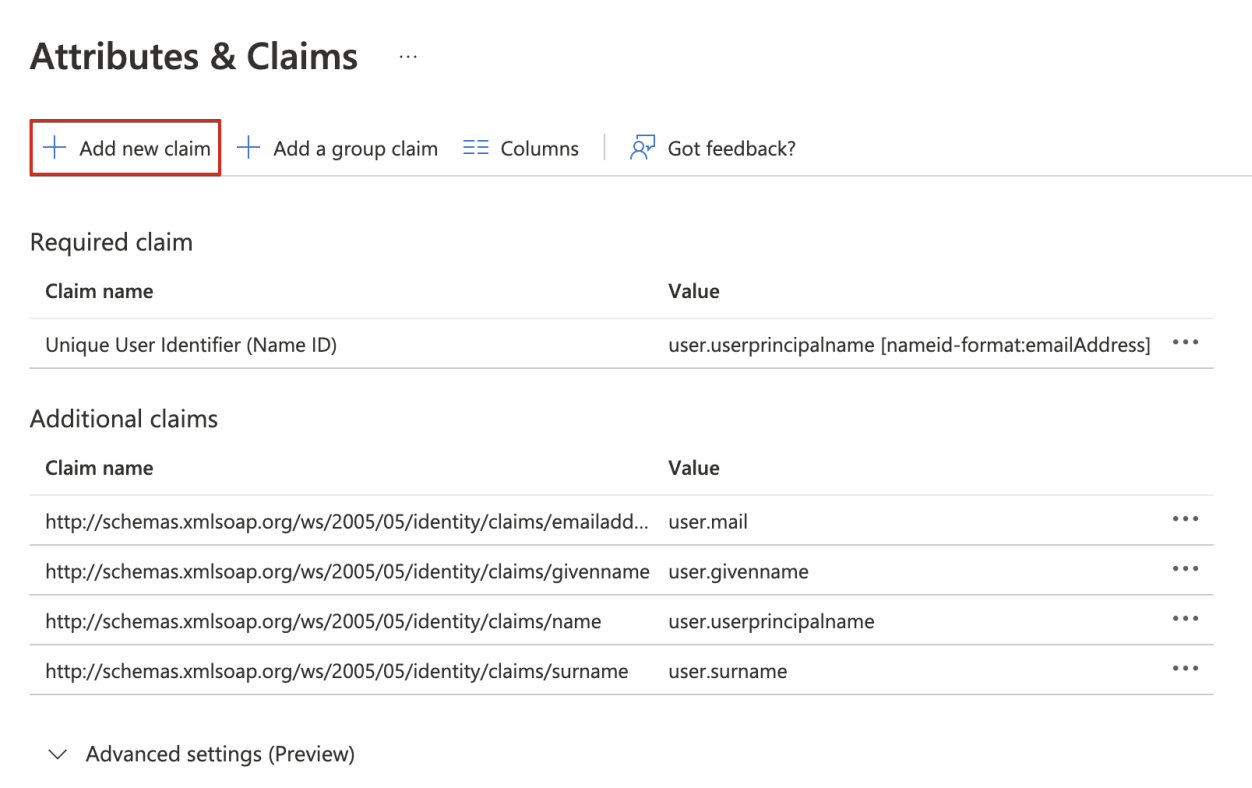
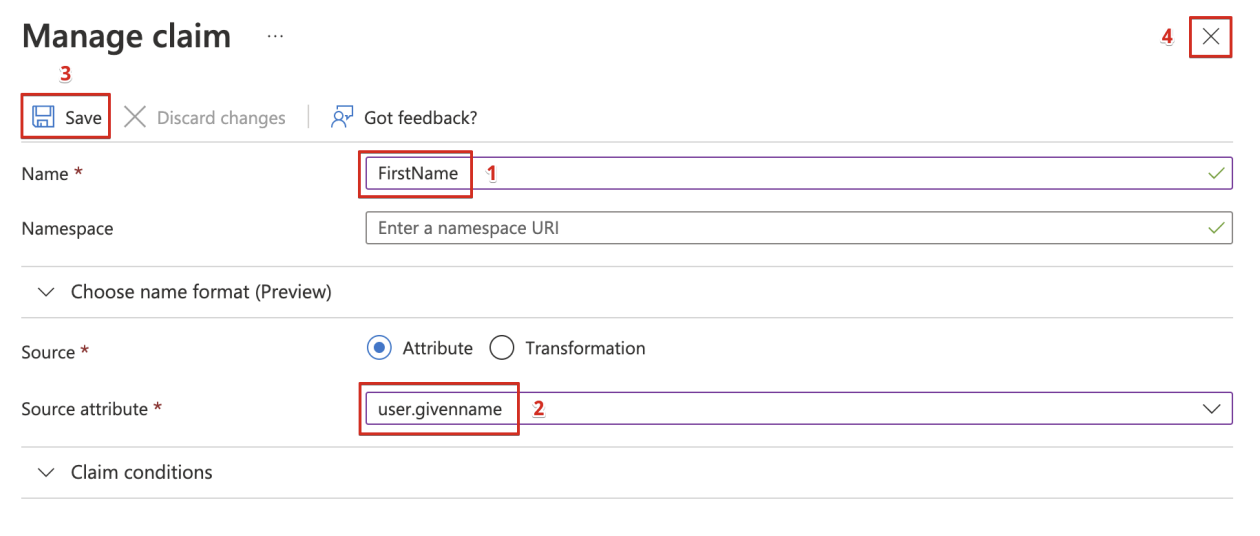
Manage the claim:
i. Enter FirstName in the Name field.
ii. Select user.givenname as the Source attribute.
iii. Click Save.
iv. Close the Manage claim window.
Add another claim:
i. Click + Add new claim.
ii. Enter a LastName in the Name field.
iii. Select user.surname as the Source attribute.
iv. Click Save.
v. Close the Manage claim window.
In the Test single sign-on with Fivetran modal, click No, I'll test later.
In the left menu, go to Users and groups.
Click Add user.
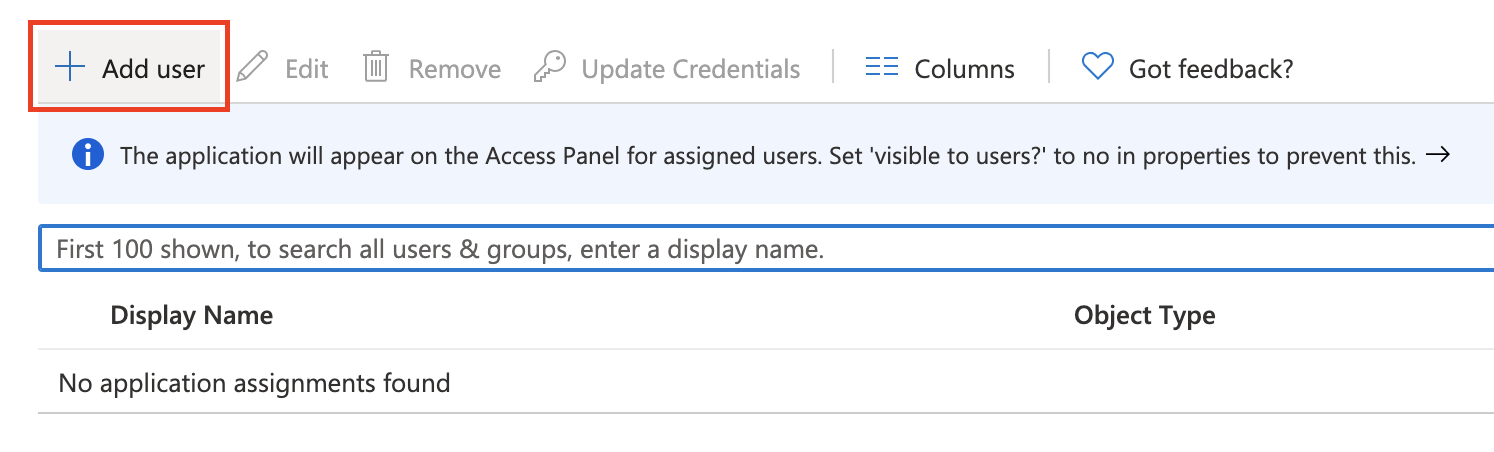
Click on the Users list item and add the users to whom you want to grant access to Fivetran. Then, click Assign.

Get Sign on URL, Issuer, Public certificate, and Application identifier
To complete setup in Fivetran, you need the Sign on URL, Issuer, Public certificate, and Application identifier. Follow these steps to get them:
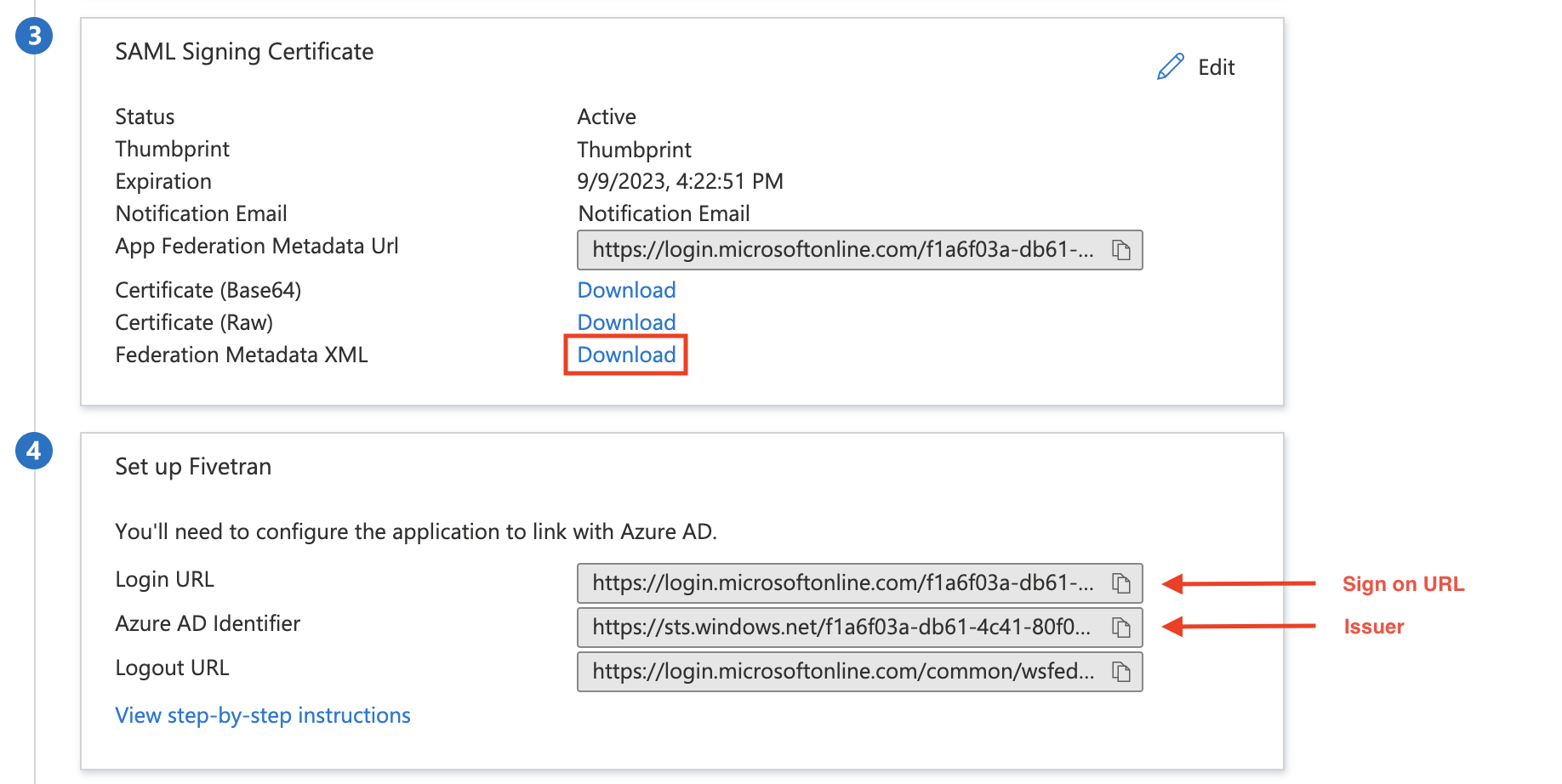
Return to the Single sign-on page of your Fivetran application in Microsoft Entra ID.
Make a note of the Identifier (Entity ID). This is Application identifier (Entity ID) in Fivetran.
Make a note of the Login URL. This is Sign on URL in Fivetran.
Make a note of the Microsoft Entra ID Identifier. This is the Issuer in Fivetran.
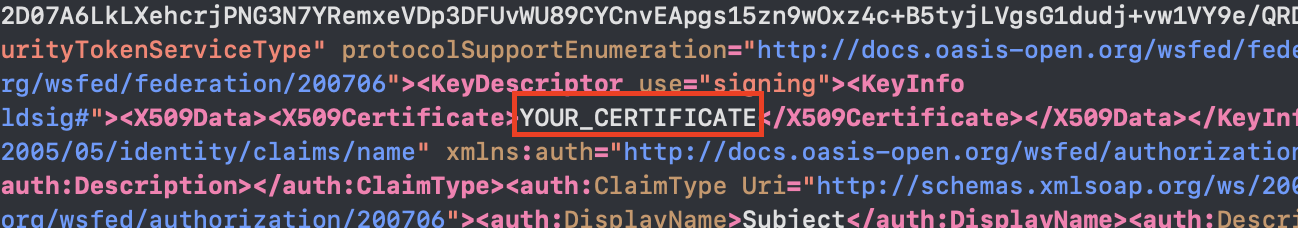
To get the Public certificate, download the Federation Metadata XML file.
Open the downloaded Federation Metadata XML file in any text editor. The certificate is a string inside the X509Certificate XML tag. Make a note of it. You will enter it in the Public certificate field in Fivetran.
In Fivetran
NOTE: By default, Fivetran allows Just-In-Time (JIT) user provisioning. If you don't have a Fivetran user for the specified Microsoft Entra ID user, the Fivetran user will be created automatically with the read-only access. To grant the newly created user the relevant role with the corresponding permissions, log in as a Fivetran user with the Users: Manage permission and manage the user's roles and permissions on the Users tab of the Users & Permissions page.
In Fivetran, click Account Settings > General.
On the Account Settings tab, under Authentication Settings, switch the Enable SAML authentication toggle to ON.
Under SAML Config, in the Sign on URL, Issuer, Public certificate, and Application identifier (Entity Id) fields, enter the values you found in Step 2.
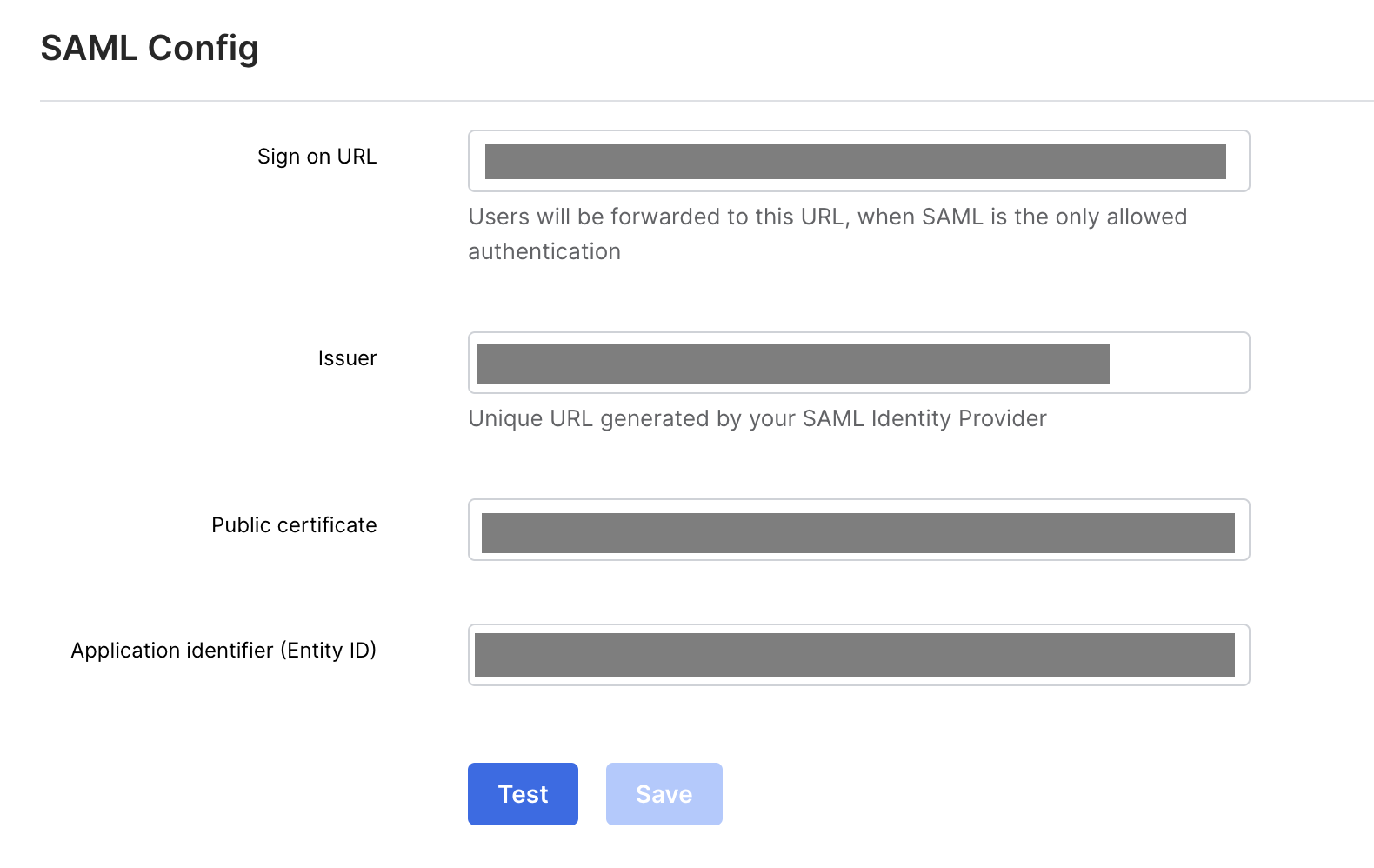
Click Save Config. You'll see the message Account settings successfully saved.
Testing SSO (Optional)
To test SSO, follow these steps:
- Go to https://myapps.microsoft.com.
- Log in to the account you have granted access to.
- Click the Fivetran button. You will be redirected to your Fivetran dashboard.
Restrict login to SSO
Follow the steps below to restrict logins to SSO only:
- Log in to the Fivetran dashboard.
- In the bottom left menu, click Account Settings > General.
- Go to the Account Settings tab.
- In the Authentication Settings section, set the Required authentication type to SAML or Google OAuth.
NOTE: When the Required authentication type is set to None, users can log in either with SSO or with their email and password.