Configuring HVR Agent From Browser
This section describes the steps to configure the HVR Agent service from a browser. For steps to configure the agent service from the Command Line Interface (CLI), see Configuring HVR Agent from CLI.
- To configure the agent service, the HVR Agent must be installed and running.
- To access the Agent Service Configuration dialog, the agent service must either be in the 'setup mode' or you must provide agent administrator (AgentAdmin) credentials.
- The Agent Service Configuration dialog can be accessed while creating a location (see Step 2. Select Agent Connection) or by editing an existing location's agent service connection properties in the Location Details page.
If the configuration for an existing agent service is modified/updated, ensure to reflect those changes in all locations that use this agent service. For example, if the password of an agent user is updated, then that user's password must be updated in all locations that use this agent service.
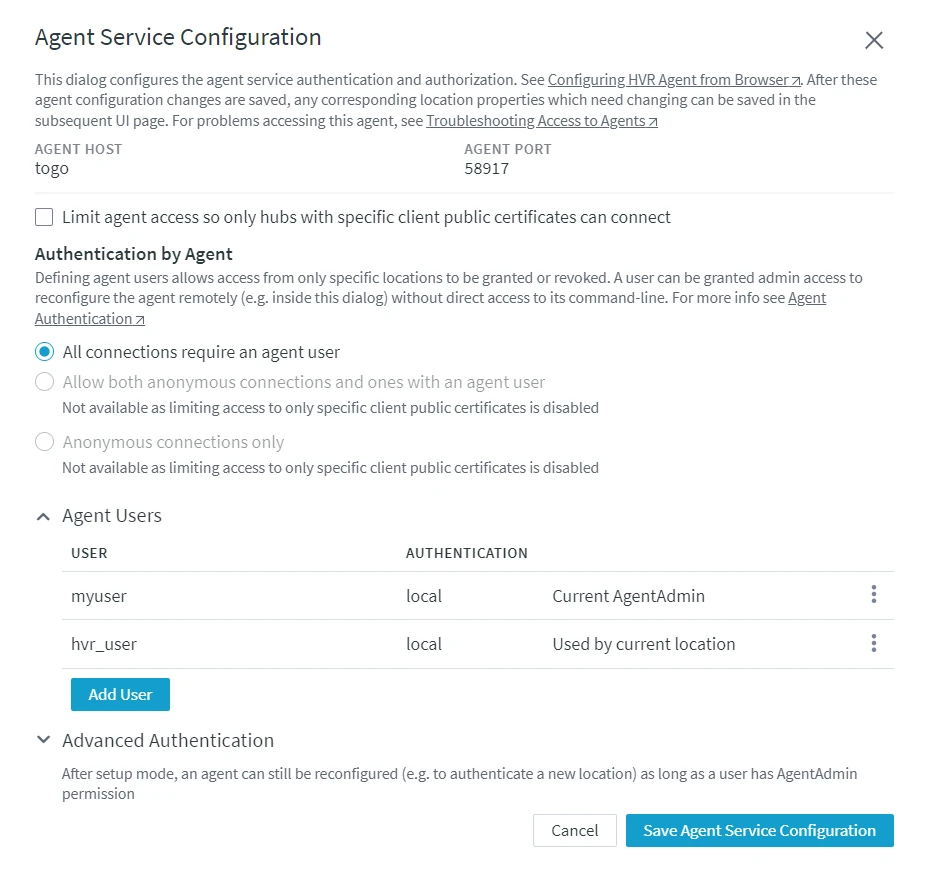
Configuring Agent Service
Perform the following steps to configure the agent service:
If the managed secrets feature is enabled, an option USE TOKEN INSTEAD is displayed in all UI fields designated for entering secrets.
Limit Agent Access
By default, the agent can be accessed by all hub system(s). However, you can also choose to allow only certain hub system(s) to access the agent service by using the client public certificate of the hub system. Selecting this option enables anonymous connections from the specified hub system(s) to the agent i.e. the hub system can connect to the agent without using the agent user credentials instead the client public certificate of the hub system is used for authentication (see step 2. Set Agent Authentication Mode).
This step is optional.
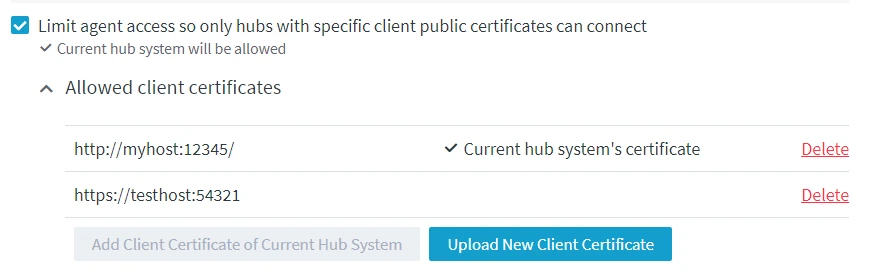
Select Limit agent access so only hubs with specific client public certificates can connect to allow only certain hub system(s) to connect to this agent. When this option is selected, the client public certificate (Agent_Client_Public_Certificate) of the current hub system is added to the list of allowed client certificates by default.
Steps to add other hub system(s) to the allowed list.
To add a hub system client certificate to the allowed list:
Create a public certificate file of the HVR Hub System. Execute the command hvrreposconfig on the hub machine that needs to be added to the allowed list:
hvrreposconfig 'Agent_Client_Public_Certificate>@file_name.pub_cert'hvrreposconfig "Agent_Client_Public_Certificate>@file_name.pub_cert"Copy the public certificate file (file_name**.pub_cert**) to the agent machine.
Add the public certificate file to the allowed list:
- In the Agent Service Configuration dialog, click Upload New Certificate.
- In the Upload Client Certificate dialog, specify the description for the hub system (e.g. its URL), then click Upload Public Certificate and add the public certificate file (file_name**.pub_cert**).
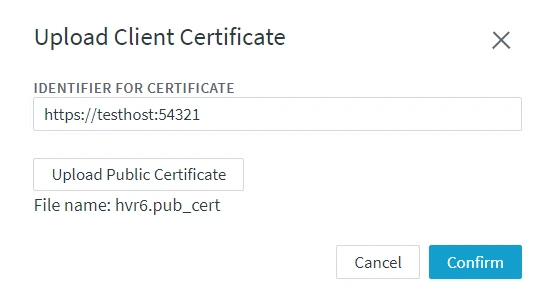
- Click Confirm. The client certificate will be added under the Allowed Client Certificates.
Set Agent Authentication Mode
This setting allows you to select the agent authentication mode for connecting a hub to the agent. For more information about agent connection authentication mode, see Agent Connection Modes.
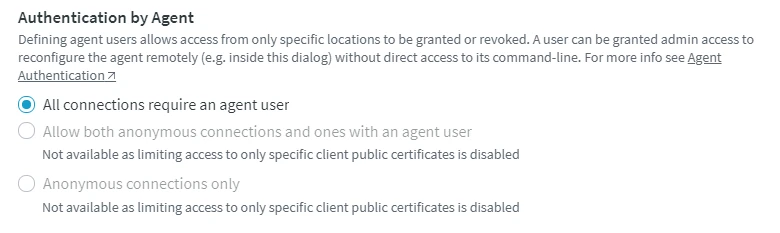
- Under Authentication by Agent, select the required connection authentication mode for the agent service.
All connections require an agent user
This authentication mode requires at least one agent user to be defined (see step 3. Add Agent User) for the agent.
Allow both anonymous connections and ones with an agent user
This authentication mode is available only if option Limit agent access so only hubs with specific client public certificates can connect is selected in step 1. Limit Agent Access.
Anonymous connections only
This authentication mode is available only if option Limit agent access so only hubs with specific client public certificates can connect is selected in step 1. Limit Agent Access.
When there are agent users already added and the agent service is configured to allow connections with agent user (using option All connections require an agent user or Allow both anonymous connections and ones with an agent user), if you then switch to Anonymous connections only, it is required to delete the existing user(s). In this case, a popup dialog asking to delete all existing agent user(s) will be displayed.
Add Agent User
An agent user is required for authenticating the connection from the hub to the agent. And, also the agent user is required for configuring the agent service from a browser (without initiating the 'setup mode'). For more information about agent users, see Agent Users.
The Agent Users section is not available if the agent authentication mode is set to Anonymous connections only in step 2. Set Agent Authentication Mode.
Under Agent Users, click Add User.
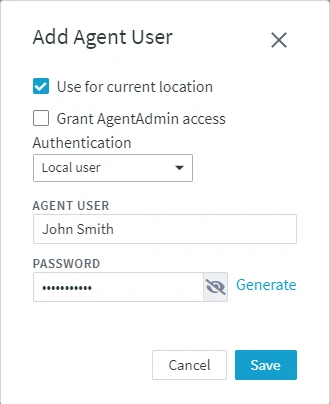
In the Add Agent User dialog, select either of the following options:
Select Use for current location if you want to use this user's credentials (AGENT USER and PASSWORD) for authenticating the connection to the agent from the current location.
When the agent user is defined to be used for a location (when Use for current location is selected), the AGENT USER and PASSWORD are stored in the location properties Agent_User and Agent_Password respectively.
Select Grant AgentAdmin access if you want to grant agent administration permissions for this user. The AgentAdmin permissions allows an agent user to configure the agent service without initiating the agent setup mode.
It is not allowed to use a user for current location and as agent administrator at the same time. The options Use for current location and Grant AgentAdmin access should not be selected at same time for a user.
Select the user Authentication method. For more information about user authentication methods, see User Authentication.
The available options are:Kerberos principal
The advanced Kerberos authentication settings is available under the Advanced authentication section.Local user
PAM user
Linux/UnixFor PAM user authentication, the default PAM service is login. To use a different PAM service, you need to configure the PAM authentication settings available under the Advanced authentication section.
Plugin user
Windows user
Windows
Specify the username, password (if required) or the Kerberos client principal (if applicable).
Click here for more information.
If the Authentication method is set to Local user or Plugin user or PAM user or Windows user,
Enter a user name in AGENT USER.
Enter a PASSWORD for the agent user or generate a random 16-character password by clicking Generate.
The minimum password length for Local user must be 10 characters.
- If the Authentication method is set to Kerberos principal, enter the name of the Kerberos client principal in LOCATION CLIENT PRINCIPAL.
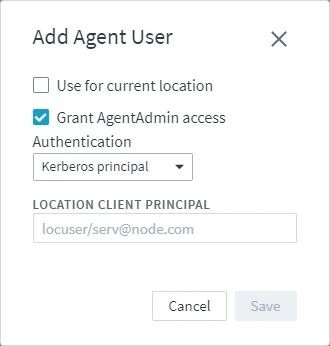
Click Save.
Set Advanced Authentication Options
This section of the configuration dialog displays the advanced authentication options for the agent (used when connecting hub to the agent service). These options affect agent's authentication system only when agent users configured with PAM or Kerberos authentication is involved in the connection.
This step is optional.
Under the Advanced authentication section, set the required advanced authentication options.
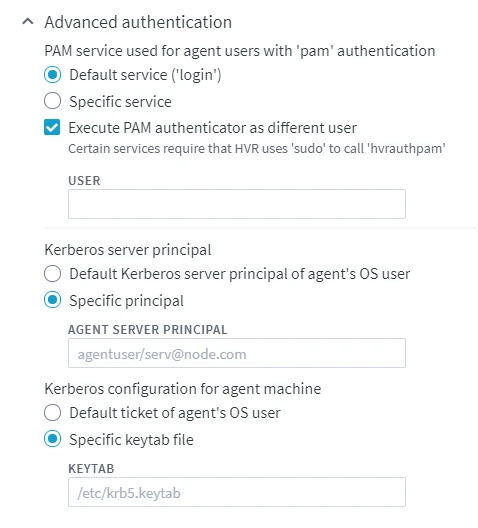
Advanced Authentication Options for PAM
The following options are applicable only when the agent authentication involves an agent user whose Authentication is set to PAM user.
- Default service ('login')
default: Use the default PAM service login for authentication. - Specific service : Use a user specified PAM service for authentication instead of the default service. Enter the name of a specific PAM service that you want to use for authentication.
Execute PAM authenticator as different user : Run the PAM authenticator as the specified USER instead of the operating system user under which the HVR Agent is running.
This user must have privilege to run the following command:
$ sudo -n -u PAM_Sudo_User -- $HVR_HOME/lib/hvrauthpam PAM_Service
Advanced Authentication Options for Kerberos
The following options are applicable only when the agent authentication involves an agent user whose Authentication is set to Kerberos principal.
The Kerberos authentication is not supported on Windows. So these options are not available for the HVR Hub or Agent installed on Windows.
Kerberos server principal
- Default Kerberos server principal of agent's OS user
default: For authentication, use the default Kerberos server principal of the operating system user under which the HVR Agent is running. - Specific principal : Use a user specified Kerberos server principal for authentication instead of the default server principal. Enter the name of a specific Kerberos server principal that you want to use for authentication.
- Default Kerberos server principal of agent's OS user
Kerberos configuration for agent machine
- Default ticket of agent's OS user
default: For authentication, use the default Kerberos ticket of the operating system user under which the HVR Agent is running. - Specific keytab file : Use a user specified Keytab file for authentication instead of the default Kerberos ticket. Enter the name of a keytab file (with complete file path) that you want to use for authentication.
- Default ticket of agent's OS user
Managing Agent Users
The following options to manage agent users are available under the More Options icon ![]() related to each user.
related to each user.
Change - Change agent user properties like Use for current location and Grant AgentAdmin access.
It is not allowed to use a user for current location and as agent administrator at the same time. The options Use for current location and Grant AgentAdmin access should not be selected at same time for a user.
Use for Current Location - Use this user's credentials for authenticating the connection to the agent service.
Delete - Delete the selected agent user.
Changing Agent User Password
To change the password of the agent user with Local user authentication, use the command hvragentuserconfig with option -p.
Example:
hvragentuserconfig -p myagentusername
Supply new password for the agent user when prompted.