Google Cloud SQL for PostgreSQL Setup Guide
Follow these instructions to replicate your Google Cloud SQL for PostgreSQL database to your destination using Fivetran.
Prerequisites
To connect your Google Cloud SQL for PostgreSQL database to Fivetran, you need:
- PostgreSQL version 9.6 - 17
- Your database's port (usually
5432) - TLS enabled on your database, if you choose to connect directly to Fivetran. Follow Google Cloud's TLS setup instructions to enable TLS on your database.
Setup instructions
Choose connection method
To connect Fivetran to your Google Cloud SQL for PostgreSQL database, do one of the following:
Connect directly (TLS required)
You must have TLS enabled on your database to connect directly to Fivetran.
Allow unsecured connections to your database.
Go to your Google Cloud Platform SQL dashboard.
Click on the name of the database that you want to connect to Fivetran.
If you plan to create a read replica to connect to Fivetran, then edit the primary database you plan to replicate. The primary database's settings will be propagated to the replica.
In the left menu, go to the Connections tab.
Go to the Security tab.
- If you see Only secured connections are allowed to connect to this instance, click Allow unsecured connections.
- If you see Unsecured connections are allowed to connect to this instance, you do not need to change anything.
Connect using Google Cloud Virtual Machine
Create a Google Cloud Virtual Machine to act as a proxy to connect. Use one of the following options:
Google Cloud SQL Proxy. To set up your GCS Proxy, set up your VM host and add Fivetran's public SSH key to your
authorized_keysfile. Install the Google Cloud Proxy on that VM.Certificate forwarding using stunnel
SSH tunneling with client certificates configured
Connect using Google Cloud Private Service Connect
You must have a Business Critical plan to use Google Cloud Private Service Connect.
Google Cloud Private Service Connect allows VPCs and Google-hosted or on-premises services to communicate with one another without exposing traffic to the public internet. Learn more in Google Cloud's Private Service Connect documentation.
Follow our Google Cloud Private Service Connect setup guide to configure Private Service Connect for your database.
Configure client certificate (optional)
Fivetran supports connecting with a client certificate if you connect through either Private networking or connecting directly.
Expand for instructions
Follow the instructions in the Google Cloud Platform SQL service to create a client certificate.
Download the
client-key.pemandclient-cert.pemfiles to a secure location. You will need them to configure Fivetran.
The
client-key.pemandclient-cert.pemfiles are only available to download during the client certificate creation.In the left menu of your Google Cloud SQL dashboard, go to the Connections tab.
Click Security in the Connections section.
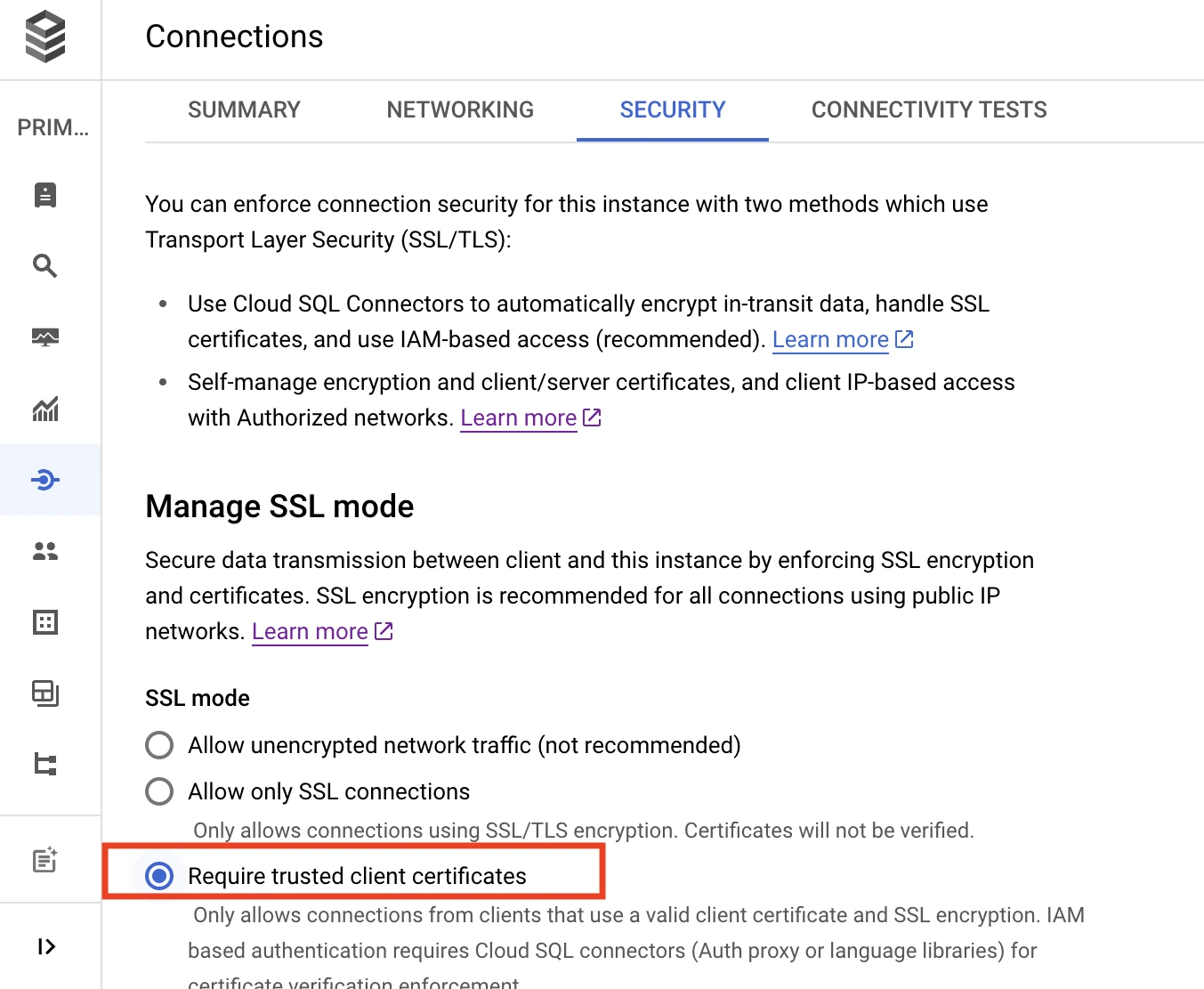
Select Require trusted client certificates under the Manage SSL mode section.
Create read replica (optional)
If you'd like, create a read replica for Fivetran's exclusive use. Using a read replica allows Fivetran to integrate your data without putting unnecessary load on or interrupting the queries running on your primary server. We recommend that you connect a read replica to Fivetran, but it's not required.
If you already have a read replica or want to connect Fivetran to your primary database, skip ahead to Step 4.
Go to your Google Cloud Platform SQL dashboard.
Click on the name of your primary database.
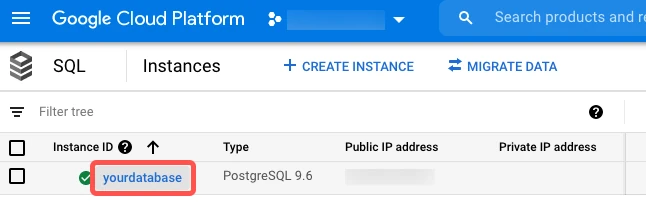
In the left menu, go to the Replicas tab.
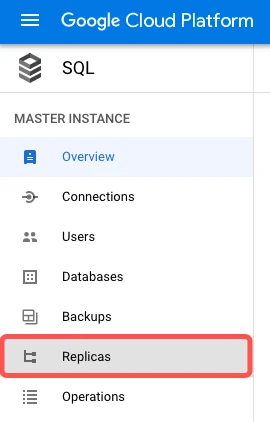
Click Create Read Replica.
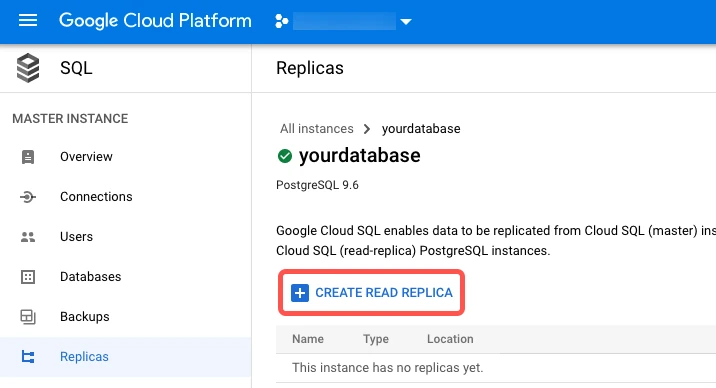
On the Create read replica page, enter an Instance ID for the replica.
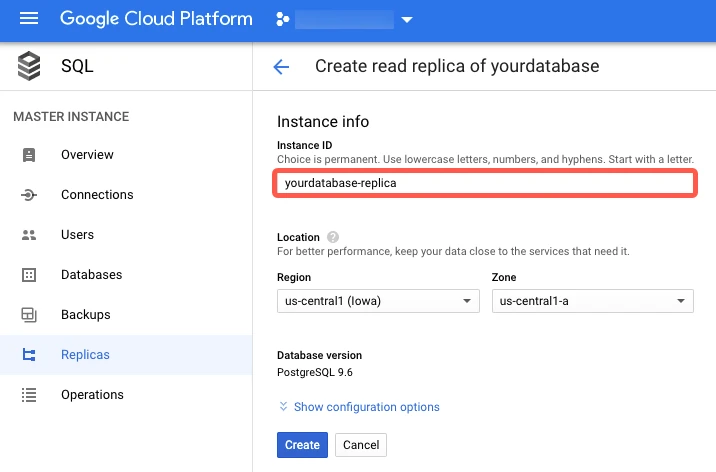
Click Done.
Click Create. It will take a few minutes for the read replica to be created.
Enable database access
Grant Fivetran's data processing servers access to your database.
In your Google Cloud Platform SQL dashboard, click on your primary database or read replica.
In the left menu, go to the Connections tab.
In the Connectivity section, click Add network.
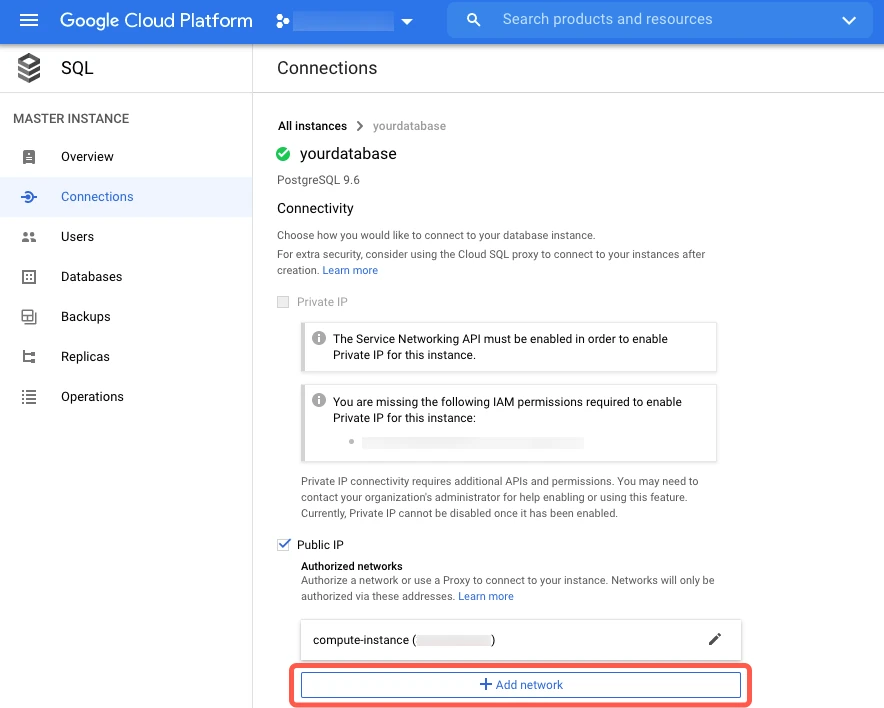
In the New network window, create a network for Fivetran. What you enter in the Network field depends on whether you're connecting directly or using an SSH tunnel.
- If you're connecting directly, enter Fivetran's IPs for your database's region.
- If you're connecting using an SSH tunnel, enter
{your-ssh-tunnel-server-ip-address}/32.
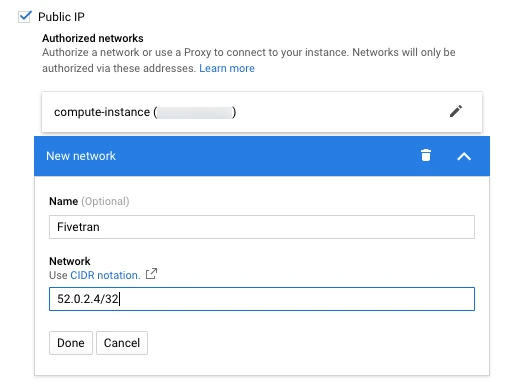
Click Save. It will take a few minutes for the database to be updated with the new settings.
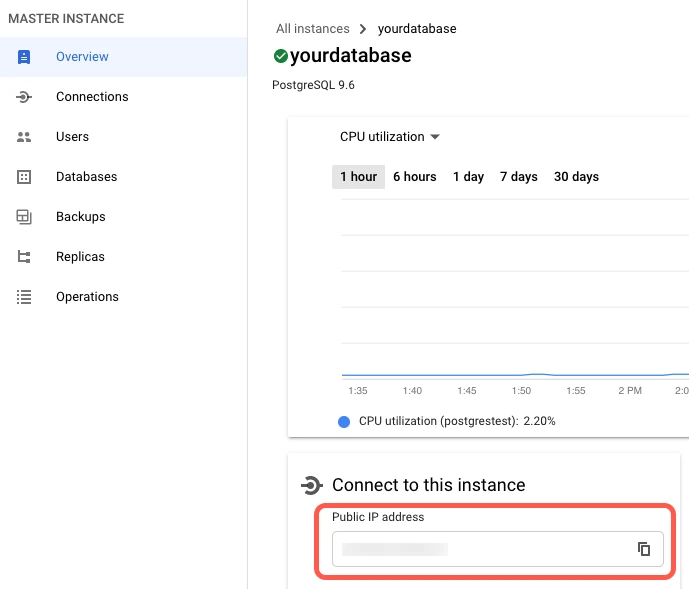
In the left menu, go to the Overview tab.
In the Connect to this instance section, find your database's public IP address and make a note of it. You will need it to configure Fivetran.
Create user
Create a database user for Fivetran's exclusive use.
Open a connection to your PostgreSQL primary database in a PostgreSQL console (such as a SQL workbench or psql).
Create a user for Fivetran by executing the following SQL command. Replace
<username>andsome-passwordwith a username and password of your choice.CREATE USER <username> PASSWORD 'some-password';
Grant read-only access
Grant the Fivetran user read-only access to all tables by running the following commands. To grant access to a schema other than PostgreSQL's default public schema, replace public with the schema name.
GRANT USAGE ON SCHEMA "public" TO <username>;
GRANT SELECT ON ALL TABLES IN SCHEMA "public" TO <username>;
ALTER DEFAULT PRIVILEGES IN SCHEMA "public" GRANT SELECT ON TABLES TO <username>;
The last command makes sure that any future tables will be accessible to Fivetran.
If you want to grant access to multiple schemas, you must run these three commands for each schema.
Restrict access to tables (optional)
If you want to limit Fivetran's access to your tables, grant the Fivetran user access to only the tables that you would like to sync. You must individually grant access to each table that you want to sync. You cannot grant access to all tables and then revoke access for a subset of tables.
Ensure that the Fivetran user has access to the schema that contains your table(s).
GRANT USAGE ON SCHEMA "some_schema" TO <username>;Revoke any previously granted permission to all tables in that schema.
ALTER DEFAULT PRIVILEGES IN SCHEMA "some_schema" REVOKE SELECT ON TABLES FROM <username>; REVOKE SELECT ON ALL TABLES IN SCHEMA "some_schema" FROM <username>;Repeat the following command for each table that you want Fivetran to sync.
GRANT SELECT ON "some_schema"."some_table" TO <username>;By default, any tables that you create in the future will not be accessible to the Fivetran user. To grant access to new tables, run the following command.
ALTER DEFAULT PRIVILEGES IN SCHEMA "some_schema" GRANT SELECT ON TABLES TO <username>;
Restrict access to columns (optional)
If you want to limit Fivetran's access to the columns in your tables, grant the Fivetran user access to only certain columns. You must individually grant access for each column that you want to sync.
Revoke any previously granted permission to read all columns in that table.
REVOKE SELECT ON "some_schema"."some_table" FROM <username>;Grant permission to the specific columns you want to sync (for example,
some_columnandother_column).If you chose Query-Based as your incremental sync method, you must grant us access to the hidden system columns
xminandctid. This speeds up your initial sync and enables capturing deletes.GRANT SELECT (xmin, ctid, some_column, other_column) ON "some_schema"."some_table" TO <username>;
Once you restrict access to columns within a table, the Fivetran user will not have access to any new columns added to that table in the future. To grant access to new columns, you must rerun the command above.
Configure incremental sync method
To keep your data up to date after the initial sync, Fivetran offers multiple incremental sync methods. These methods track recent data changes so Fivetran can sync only what changed since the last sync instead of copying entire tables each time. Learn more in our Updating data documentation.
We recommend using the Logical replication method when possible because it is faster and more efficient than Query-Based. For guidance on choosing the best option for your workload, see Logical replication vs Query-Based documentation.
Configure your chosen incremental sync method:
Logical replication
You can only enable logical replication if your PostgreSQL version is 10 or later. If you want to use logical replication on a read replica, your PostgreSQL version must be 16 or later.
Logical replication relies on the logical decoding of the PostgreSQL write-ahead log (WAL). Fivetran reads the WAL using the pgoutput plugin to detect any new or changed data. This plugin replicates data from your custom publication without needing additional libraries. Learn more in our logical replication documentation.
To enable logical replication, follow these steps:
Ensure that your server has ample free space for the logs. Logs that Fivetran has already processed are released. However, logs are not released if replication stops (for example, if we lose access). In this case, logs may accumulate on your server and consume additional storage. The amount of additional disk space consumed by these logs is proportional to the amount of changes committed on the server. If a lost connection can't be resumed quickly enough, you can drop the replication slot, which releases the storage of unconsumed logs. You would then need to do a full re-sync of your connection to reset the cursor in the replication slot.
In your Google Cloud platform SQL dashboard, set the
cloudsql.logical_decodingflag toon.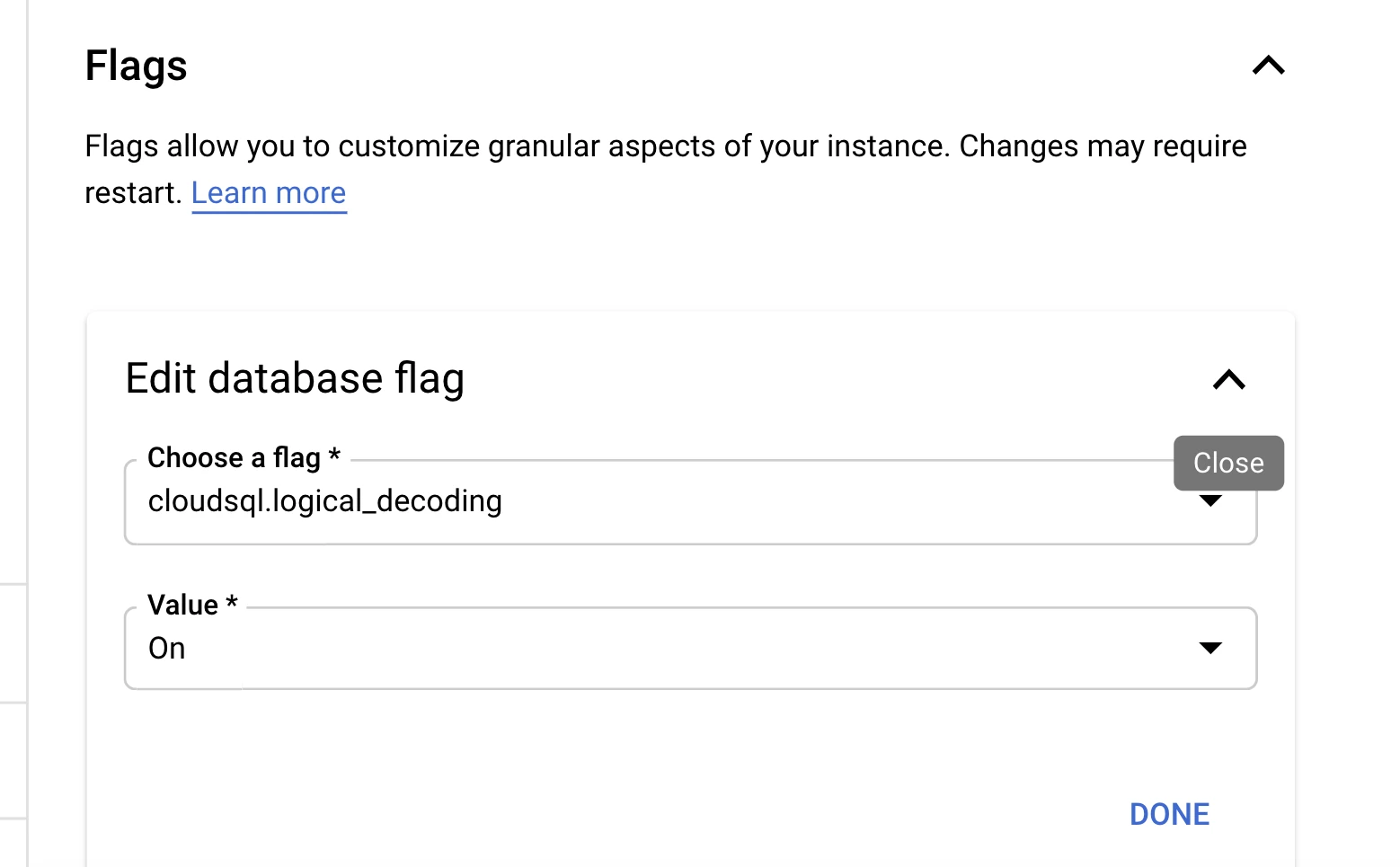
Click Done to save the change.
Go into your primary Cloud PostgreSQL database as a cloudsqlsuperuser (
postgresby default in Google Cloud SQL).If your superuser doesn't have permission to create a replication slot, run the
alter user postgres with replication;command before you do the following steps.Ensure that the
statement_timeoutsetting on your server is either0(the default value to disable the timeout) or greater than5 minute.Do not change the
wal_sender_timeoutparameter in your database. If you change thewal_sender_timeout, it will automatically reset to the default value when your session ends.Create a publication for your tables. If you want, you can create a publication for only certain tables so that you add or remove tables from the publication later on. Only changes from tables in the publication are replicated to Fivetran. Each database can have multiple distinct publications. You must have
CREATEprivileges or above to run this command.The publication name
fivetran_pubquoted throughout this guide is used purely as an example. The actual publication name should be unique for every database and cannot start with a number.CREATE PUBLICATION fivetran_pub FOR TABLE table2, table4, table8;To add or remove a table from a publication, run the following command. You must have the ownership rights over the table(s).
ALTER PUBLICATION fivetran_pub ADD/DROP TABLE table_name;Alternatively, you can create a publication for all of your tables. However, you cannot remove any table from this publication later on. You must have cloudsqlsuperuser privileges to run this command.
CREATE PUBLICATION fivetran_pub FOR ALL TABLES;(Optional) You can choose which operations to include in the publication. For example, the following publication includes only
INSERTandUPDATEoperations.CREATE PUBLICATION insert_only_pub FOR TABLE table1 WITH (publish = 'INSERT, UPDATE');To add partitioned tables for PostgreSQL version 13 or later, run the following command to enable publish_via_partition_root.
CREATE PUBLICATION fivetran_pub FOR ALL TABLES WITH (publish_via_partition_root=true);Create a logical replication slot for the database you want to sync by running the following command. You must use the standard output plugin
pgoutput. Ensure that you are connected to the correct database when you create your replication slot, or your connection will not be able to find the slot.You must create a unique replication slot for every connection that uses the same PostgreSQL cluster. Replication slot names cannot start with a number. (The replication slot name
fivetran_pgoutput_slotquoted throughout this guide is used purely as an example.)You need to create the replication slot after you have created the publication.
SELECT pg_create_logical_replication_slot('fivetran_pgoutput_slot', 'pgoutput');If your PostgreSQL server version is 16 or later and you want to sync from a standby, create the replication slot in the read replica.
Verify that your chosen tables are in the publication.
SELECT * FROM pg_publication_tables;Grant the Fivetran user permission to read the replication slot.
ALTER ROLE fivetran WITH REPLICATION;Log in as the Fivetran user.
Verify that the Fivetran user can read the replication slot by running the following command. Replace
fivetran_pgoutput_slotwith your replication slot name andfivetran_pubwith the publication name.SELECT count(*) FROM pg_logical_slot_peek_binary_changes('fivetran_pgoutput_slot', null, null, 'proto_version', '1', 'publication_names', 'fivetran_pub');
If the query succeeds, then permissions are sufficient.
Query-Based
Fivetran runs SQL queries that read PostgreSQL system columns (xmin and, when applicable, ctid) to detect new and changed data during each sync.
Capture Deletes (optional)
By default, Query-Based sync detects new and updated rows. If you also want to detect deleted rows, you can turn on Capture Deletes in the connection setup form.
When you enable Capture Deletes:
Fivetran adds an internal helper column
ctid_fivetran_idto each synced table. Fivetran uses this column to track deletes by storing the row'sctidvalue at the end of each sync.- Before the initial sync (new connection): Fivetran creates tables with
ctid_fivetran_idduring the initial sync (no additional re-sync). - After data is already synced (existing connection): Fivetran runs a one-time re-sync of the selected tables to add
ctid_fivetran_id.
- Before the initial sync (new connection): Fivetran creates tables with
This setting is permanent for the connection. After you click Save & Test, it's locked and can’t be disabled later, whether or not the connection has run its first sync.
For details and limitations, see our Capturing deletes documentation.
Query-Based sync requires full table scans to detect updates and may be slower than logical replication, especially for large tables. In high-write databases, PostgreSQL xmin freezing/wraparound can also cause older rows to be re-synced, increasing sync volume and load on your PostgreSQL source database. If possible, use logical replication.
For some accounts, these re-syncs may also increase MAR for that sync. To mitigate this, you can enable pg_visibility and pageinspect and create the required wrapper functions. See our FAQ page for more information.
Fivetran Teleport Sync Sunset
Fivetran Teleport Sync is a proprietary incremental sync method that can capture deletes without requiring additional setup beyond a read-only SQL connection. Updates are captured using the xmin system column. Learn more in our Fivetran Teleport Sync documentation.
If you are trying to connect with a standby or read replica, run the following SQL command on your primary database as the Fivetran user:
CREATE AGGREGATE BIT_XOR(IN v bigint) (SFUNC = int8xor, STYPE = bigint);
If you are not connecting with a read replica, you do not need to do any additional configuration. The aggregate that the Teleport mechanism will later use is automatically created for you.
Finish Fivetran configuration
In your connection setup form, enter a Destination schema prefix. This is used as the connection name and cannot be modified once the connection is created.
In the Destination schema names field, choose the naming convention you want Fivetran to use for the schemas, tables, and columns in your destination:
- Source naming: Preserves the original schema, table, and column names from the source system in your destination.
- Fivetran naming: Standardizes the schema, table, and column names in your destination according to the Fivetran naming conventions.
If you want to modify your selection, make sure you do it before you start the initial sync.
Depending on your selection, we will either prefix the connection name to each replicated schema or use the source schema names instead.
In the Host field, enter your database's IP that you found in Step 4 (for example,
1.2.3.4). Alternately, you can also enter your database host's domain (for example,your.server.com).Enter your database instance's port number. The port will be
5432, unless you changed the default.Enter the Fivetran-specific user that you created in Step 5.
Enter the password for the Fivetran-specific user that you created in Step 5.
Enter the name of your database (for example,
your_database).(Hybrid Deployment only) If your destination is configured for Hybrid Deployment, the Hybrid Deployment Agent associated with your destination is pre-selected for the connection. To assign a different agent, click Replace agent, select the agent you want to use, and click Use Agent.
(Not applicable to Hybrid Deployment) Choose your connection method. If you selected Connect via an SSH tunnel, provide the following information:
- SSH hostname (do not use a load balancer's IP address/hostname)
- SSH port
- SSH user
If you connected through a Google Cloud SQL Proxy, use
127.0.0.1as the host name and the Google Cloud Proxy's external IP as the SSH host. You must also disable TLS encryption.(Optional for Direct Connection or Private Networking) Open the
client-cert.pemfile with a text editor or Terminal. Copy all the content between the-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----lines, including the lines themselves. Paste the content into the Client public certificate field in the Fivetran connection setup form.(Optional for Direct Connection or Private Networking) Open the
client-key.pemfile with a text editor or Terminal. Copy all the content between the-----BEGIN RSA PRIVATE KEY-----and-----END RSA PRIVATE KEY-----lines, including the lines themselves. Paste the content into the Client private key field in the Fivetran connection setup form.In the Update Method field, select the incremental sync method that you want to use:
- Logical Replication: Enter your Replication Slot name and Publication Name.
- Query-Based: (Optional) Set the Capture Deletes toggle to ON if you want to capture deletes. For more information, see Capture deletes.
(Not applicable to Hybrid Deployment) Copy the Fivetran's IP addresses (or CIDR) that you must safelist in your firewall.
Click Save & Test. Fivetran tests and validates our connection to your Google Cloud SQL for PostgreSQL database. Upon successful completion of the setup tests, you can sync your data using Fivetran.
Setup tests
Fivetran performs the following tests to ensure that we can connect to your Google Cloud PostgreSQL database and that it is properly configured:
- The Connecting to SSH Tunnel Test validates the SSH tunnel details you provided in the setup form. It then checks that we can connect to your database using the SSH Tunnel. (We skip this test if you aren't connecting using SSH.)
- The Connecting to Host Test validates the database credentials you provided in the setup form. The test verifies that the host is not private and then checks the connectivity to the host.
- The Validating Certificate Test generates a pop-up window where you must choose which certificate you want Fivetran to use. It then validates that certificate and checks that we can connect to your database using TLS. (We skip this test if you selected an indirect connection method and then disabled the Require TLS through Tunnel toggle.)
- The Connecting to Database Test checks that we can access your database.
- The Connecting to WAL Replication Slot Test confirms that the database associated with the replication slot matches the name you supplied in the setup form. It then verifies that the replication slot uses the
pgoutputplugin. Lastly, it makes sure that the Fivetran user has replication privileges. (We skip this test if you selected Query-Based as your incremental sync method.) - The Checking Configuration Values Test checks a set of WAL-configured values against the recommended settings and detects if they are below the recommended range. (We skip this test if you selected Query-Based as your incremental sync method.)
- The Publication Test verifies that the supplied publication name exists in your database. (We skip this test if you selected Query-Based as your incremental sync method.)
- The Query-Based Extensions Test checks that the correct extensions are enabled for the Query-Based incremental sync method. (This test is skipped if you select Logical Replication as your incremental sync method.)
The tests may take a few minutes to finish running.