Azure Private Link
You must have a Business Critical plan to use Azure Private Link.
Azure Private Link allows Virtual Networks (VNets) and Azure-hosted or on-premises services to communicate with one another without exposing traffic to the public internet. Learn more in Microsoft's Azure Private Link documentation.
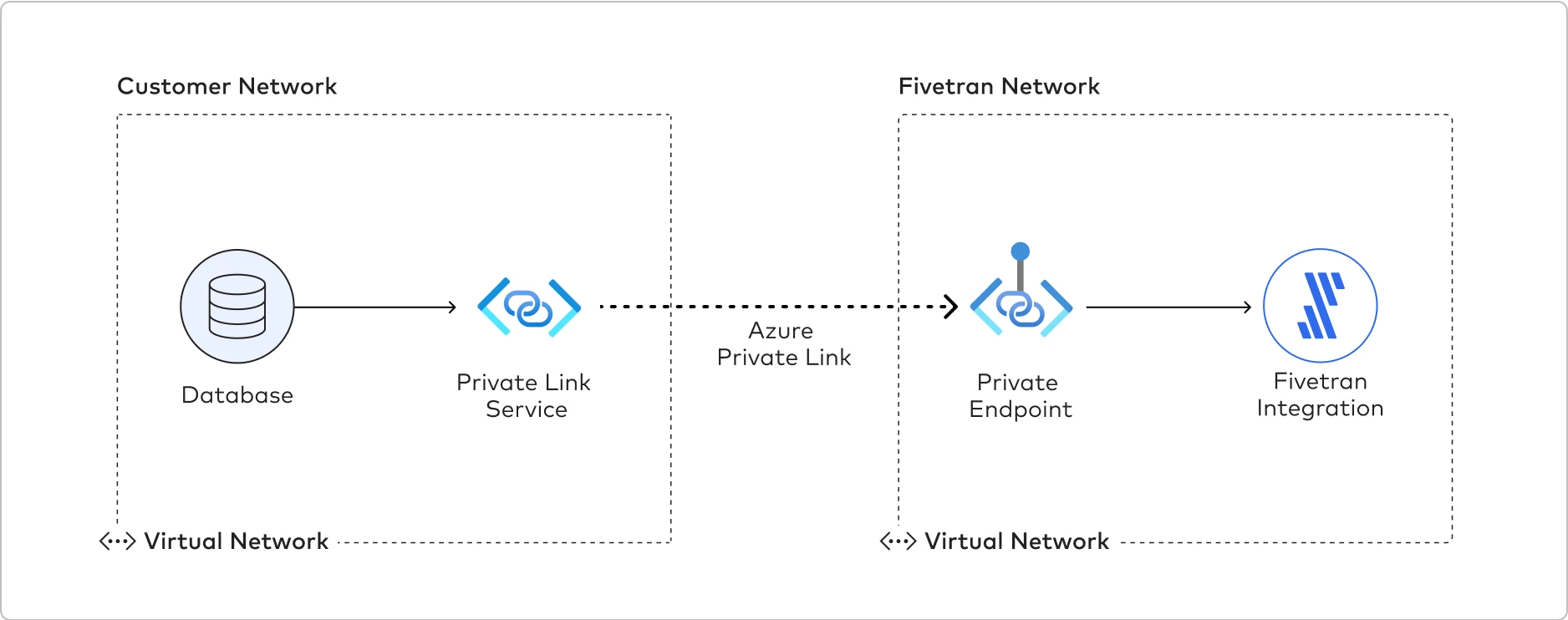
Fivetran uses Private Link to move your data securely between our system and your Azure-hosted, Azure Virtual Machine-hosted, or on-premises source. Private Link works differently depending on your source type:
- If your data source is hosted in Azure, Fivetran can connect to your source using a Private Link connection. We query and process the data from the source into our system.
- If your data source is hosted in an Azure Virtual Machine or on-premises, you can use Azure Private Link Service to connect Fivetran to your source. To use Azure Private Link Service, you must create an Azure Private Link Service with port forwarding VMs. The VMs relay the network traffic into your Azure VNet, which then connects to your source through Azure ExpressRoute or Azure VPN Gateway.
You can also use Azure Private Link with multiple destinations. See a complete list in our Supported destinations documentation.
As an extra layer of security, Fivetran enables TLS on your Private Link connection by default. We recommend that you keep TLS enabled unless you know it is safe to forgo it. To disable TLS, set the Require TLS when using Private Networking toggle to OFF.
If you set the Require TLS when using Private Link toggle to OFF, Fivetran first attempts to connect over TLS. If this fails, Fivetran automatically retries the connection in clear text. You are responsible for configuring this option according to your corporate security policies.
Prerequisites
To set up Azure Private Link, you need an Azure-hosted, Azure Virtual Machine-hosted, or on-premises source in one of our supported regions.
Your on-premises source must be one of our supported databases. See a complete list in our Databases documentation.
How you connect Azure Private Link to your source depends on whether your source is hosted in Azure, in an Azure Virtual Machine, or on-premises.
Postrequisites
To use Azure Private Link, you must select Azure as a Cloud service provider in the Finish Fivetran configuration step of the relevant destination setup guide.
Setup instructions for Azure-hosted sources
Expand for instructions
We support connecting to the following Azure-hosted sources using Private Link:
- Azure Blob Storage
- Azure Cosmos DB for MongoDB
- Azure Cosmos DB for NoSQL
- Azure Functions
- Azure Database for MariaDB
- Azure Database for MySQL
- Azure Database for PostgreSQL
- Azure SQL Database
- Azure SQL Managed Instance
The following graphic illustrates how Azure Private Link establishes a connection between the Fivetran network and the customer network. Fivetran uses Private Endpoints to establish a Private Link with the Azure Database for MySQL and Snowflake.
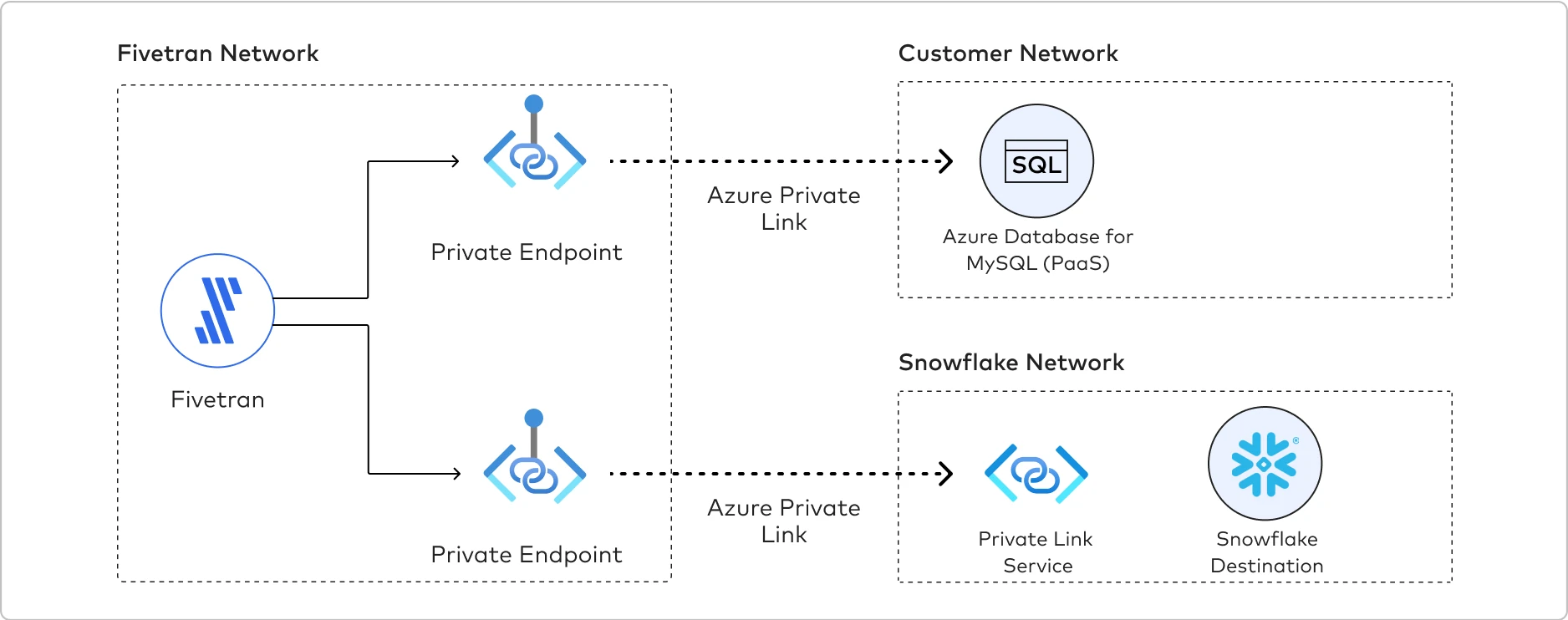
To establish a Private Link connection, do the following:
- Verify that your Azure-hosted source supports Private Endpoint in Microsoft’s Private Endpoint documentation.
- Create a Fivetran support ticket and provide your Azure-hosted service’s fully-qualified resource ID, including the resource name and resource type of your Azure-hosted source.
- Wait to receive Private Endpoint request details from Fivetran. We create a Private Endpoint using your resource ID, type, and subresource. We then initiate a Private Link connection request as part of the Private Endpoint setup and share the details of that request with you.
- In the Azure Portal or CLI, verify and approve the Private Link connection request from Fivetran. Fivetran then finishes setting up Private Link for your Azure-hosted service on our side.
Setup instructions for Azure Virtual Machine-hosted or on-premises sources
Expand for instructions
How you set up Private Link for your Azure Virtual Machine-hosted or on-premises source depends on whether or not your source already has an Azure Private Link Service.
If your source is already configured with a Private Link Service, follow the setup instructions for Azure-hosted sources to complete your Fivetran setup.
If you do not have a Private Link Service yet, you will need to configure one before establishing a Private Link connection by following the steps below:
- You must have a VNet with access to your sources.
- If you are configuring your on-premises sources and they aren't connected to Azure yet, either follow the instructions in the Azure ExpressRoute documentation (recommended) or Azure VPN Gateway documentation to connect them to Azure.
- Azure ExpressRoute provides a dedicated, high-bandwidth connection between the on-premise network and Azure, bypassing the public internet.
- Azure VPN Gateway establishes a secure, encrypted VPN tunnel over the public internet between the on-premise network and Azure.
- If you are configuring your Azure Virtual Machine-based sources, ensure that they are accessible from the VNet where the Private Link Service Load Balancer will be running.
- A single Azure Private Link Service can support one or multiple sources simultaneously, with different ports mapped to their respective data source IP addresses. You must enter these ports in Fivetran's connection setup form.
- Inside the VNet, create a Standard Load Balancer with a NIC-based backend pool that has access to your data sources. Configure a health probe and a load balancer rule with the ports that your connections will use. Learn how in Azure's Create a load balancer guide.
- Create a Private Link Service associated with the load balancer that you created in step 1. Learn how in Azure's Create a private link service guide.
- Create one or more Virtual Machines and place them in the backend pool of the load balancer you created in step 1.
- Enable IP forwarding on each of the backend Virtual Machine network interfaces. Learn how to enable IP forwarding in Azure's Enable IP forwarding documentation.
- For security purposes, ensure that no public IP addresses are configured for the Virtual Machines. Private Link connections use only private IP addresses.
- (Optional) Log in to each Load Balancer-backend Virtual Machine and run the script below. The script configures Network Address Translation (NAT), which forwards network packets from SLB-backend Virtual Machines to your data sources. The script below configures a single port forwarding, but feel free to add additional sets of iptables
PREROUTINGandPOSTROUTINGrules for additional ports:
#!/bin/bash
# This script configures Network Address Translation to forward incoming packets
# from the Azure Standard Load Balancer to IP-based destinations and route them
# back. In this script, "destination" means a data source server that Fivetran connects to.
# local port where Load Balancer sends traffic to
SOURCE_PORT=<local_port>
# destination server inside internal network
DESTINATION_IP=<destination_server_ip_address>
DESTINATION_PORT=<destination_server_port>
# enable IP forwarding on host
echo 1 > /proc/sys/net/ipv4/ip_forward
# clear existing iptables rules and chains
iptables -F
iptables -t nat -F
iptables -X
# change the packet recipient from local to destination socket (host & port)
iptables -t nat -A PREROUTING -p tcp --dport ${SOURCE_PORT} -j DNAT --to-destination ${DESTINATION_IP}:${DESTINATION_PORT}
# change the source IP address from the LB NAT IP address to the IP of this LB-backend host
iptables -t nat -A POSTROUTING -p tcp -d ${DESTINATION_IP} --dport ${DESTINATION_PORT} -j SNAT --to-source $(hostname -i)
For additional help, read Microsoft’s Private Link Service documentation or create a Fivetran support ticket.
Setup instructions for self-service Fivetran accounts Beta
Expand for instructions
Self-service Private Link lets you create and manage Azure Private Links without waiting for Fivetran support to provision the network infrastructure.
Self-service Private Link is supported with Azure Private Link for the following connectors:
Find resource ID
- Verify that your source supports Private Endpoint. For more information, see Microsoft’s documentation.
- Log in to the Azure portal and then go to your Azure-hosted service.
- Select your workspace and then click on JSON View.
- Save the Resource ID. You will need it to create the Private Link connection.
Configure Private Link connection
In Fivetran's connection setup form, select Connect via private networking in the Connection Method drop-down menu.
Click + Configure a new Private Link connection.
Enter a Name for your Private Link connection.
In the Private Link Resource ID field, enter the resource ID you found in Step 1.
In the Private Link Subresource name drop-down menu, select the subresource corresponding to your resource type. The following table lists the subresources corresponding to each resource type:
Resource Type Subresource Azure Cosmos DB for MongoDB MongoDBAzure Cosmos DB for NoSQL sqlAzure SQL Database sqlServer(Optional) Click the Add DNS record manually checkbox to provide a list of private DNS record names. This should correspond to the record sets found in the private DNS zone, in the exact order in which they are listed. We recommend that you manually provide these record names to avoid any potential connection errors.
Click Create and save. Fivetran will raise a connection request in Azure.
It might take up to 10 minutes for us to raise the connection request.
Accept connection request
- Go to your Azure account.
- Go to Private Link Center > Pending connections.
- Select the connection request from Fivetran, then click Approve.
- In the pop-up window, confirm that you want to approve the connection request. Once Azure processes the request, a Connection created message will appear in Fivetran's connection setup form.
- Update your username to
<username>@dbname.