Azure Database for MySQL Database Setup Guide
You can connect Fivetran to a read replica of your Azure Database for MySQL database to ensure that we don't add any strain to your primary database. Many production environments include a read replica by default; if yours doesn't, you can create one.
Follow these instructions to replicate your Azure Database for MySQL database to your destination using Fivetran.
Prerequisites
To connect your MySQL database to Fivetran, you need:
- MySQL version 5.5 or above for non-RDS databases (5.5.40 is the earliest version tested). MySQL version 5.6.13 or above for RDS databases.
- Your database host's IP (for example,
1.2.3.4) or domain (your.server.com) - Your database's port (usually
3306) - A unique replica ID for Fivetran. We need this ID because we connect to your database as a replica. We provide a random replica ID in your setup form, but you can provide your own if you'd prefer or if the form's replica ID conflicts with one of your existing replica IDs.
The replica ID is a unique ID within the MySQL replica set. By default, the replica ID is a random integer greater than 1000.
For the prerequisites connecting using an SSH tunnel, see Fivetran's Connection Options page.
Setup instructions
Do not perform the Choose connection method step if you want to use Hybrid Deployment for your data pipeline.
Choose connection method
First, decide whether to connect Fivetran to your Azure Database for MySQL database directly, through an SSH tunnel, using Azure Private Link, or using Proxy Agent. How you configure security groups will differ based on your connection method.
Connect directly (TLS required)
You must have TLS enabled on your database to connect directly to Fivetran.
Fivetran connects directly to your database instance.
Connect using SSH
Fivetran connects to a separate server in your network that provides an SSH tunnel to your database. You must connect through SSH if your database is contained within an inaccessible subnet.
If you have an SSH connection, follow these SSH connection instructions before you proceed to the next step.
Connect using Azure Private Link
You must have a Business Critical plan to use Azure Private Link.
Azure Private Link allows Virtual Networks (VNets) and Azure-hosted or on-premises services to communicate with one another without exposing traffic to the public internet. Learn more in Microsoft's Azure Private Link documentation.
Follow our Azure PrivateLink setup guide to configure Private Link for your database.
Connect using Proxy Agent
Fivetran connects to your database through the Proxy Agent, providing secure communication between Fivetran processes and your database host. The Proxy Agent is installed in your network and creates an outbound network connection to the Fivetran-managed SaaS.
To learn more about the Proxy Agent, how to install it, and how to configure it, see our Proxy Agent documentation.
Choose incremental sync method
To keep your data up to date after the initial sync, we use one of the following incremental sync methods:
- Binary log
- Fivetran Teleport Sync
Fivetran Teleport Sync disables large, rapidly changing tables if they fail to sync. Learn more in the Teleport general limitations documentation.
Each of these methods keeps a record of recent data changes, which allows Fivetran to update only the data that has changed since our last sync.
To learn the differences between the two methods, see our incremental sync documentation.
Enable access
You must configure your firewall to grant Fivetran access to your database.
In the Azure console, select your Azure Database for MySQL resource.
Open the Connection security tab.
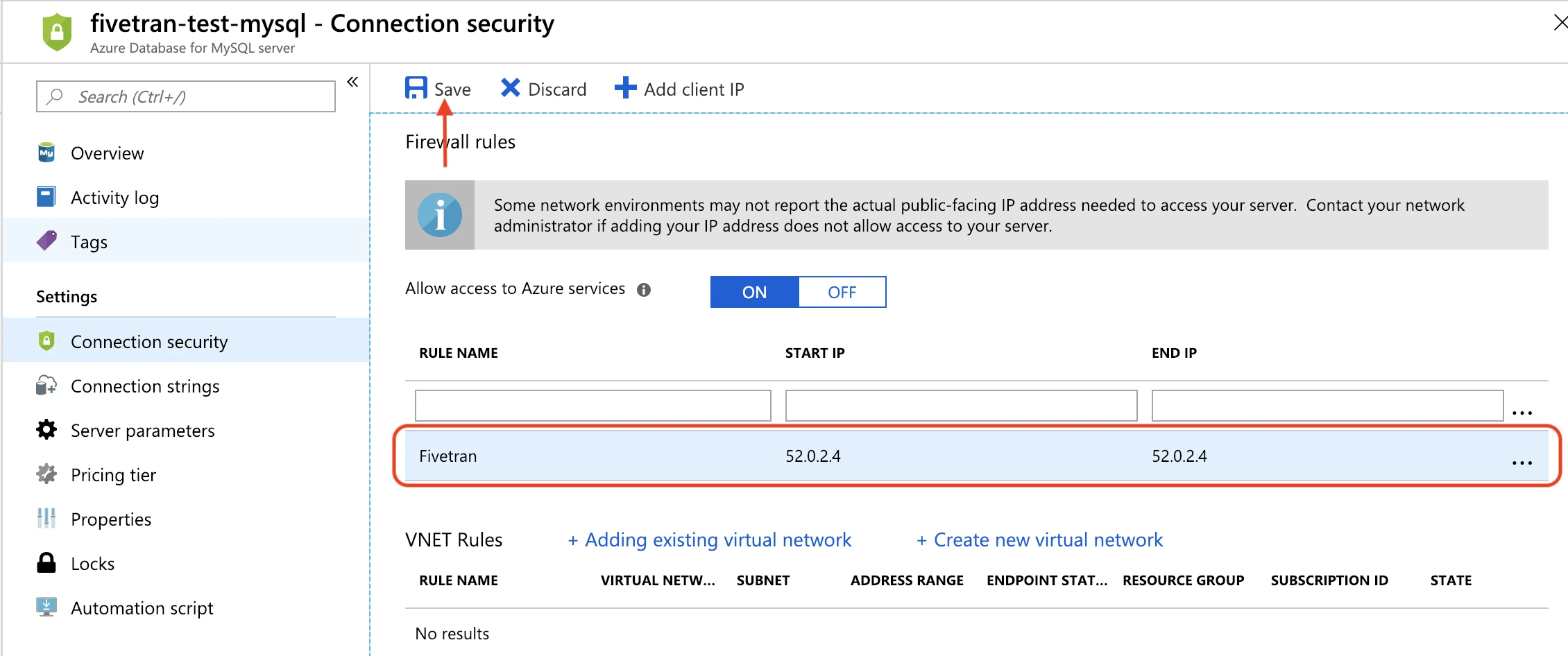
If you are connecting directly, create a new firewall rule using Fivetran's IP as both the Start IP and End IP. If you are connecting through SSH, use your tunnel server's IP.
Click Save.
Create user and configure incremental updates
Next, create a Fivetran user for your Azure Database for MySQL database. If you are connecting Fivetran to a read replica, you must create the user on your primary database because read replicas are read-only. Your read replica will inherit the user from your primary database.
This user must be reserved for Fivetran use only and must be unique to your connection. For more information, see our MySQL documentation.
How you create a user depends on which incremental sync method you are using. Follow the instructions below for your incremental sync method from Step 2:
Binary log
Open a connection to your Azure Database for MySQL database using your favorite SQL tool (for example, MySQL Workbench or the
mysqlcommand in your operating system's terminal window).Create a Fivetran user and grant replication permissions by running the following SQL commands. Replace
<username>and'password'with a username and password of your choice.CREATE USER <username>@'%' IDENTIFIED WITH mysql_native_password BY 'password'; GRANT SELECT, REPLICATION CLIENT, REPLICATION SLAVE ON *.* TO <username>@'%';You must grant the Fivetran user SELECT permissions for all of the columns in the tables that you want to sync. When we do not have SELECT access to all columns in a table, we trigger a re-sync for that table, which slows down your syncs. If you don't want to sync certain columns, you can exclude them from your syncs in the Fivetran dashboard.
If there are errors when running these commands, you may lack sufficient privileges and should contact your database administrator.
Verify that your binary log format is ROW (Azure Database for MySQL's default format). If not, set the binary log format to ROW in your Azure portal. Fivetran needs ROW format binary logs to perform incremental updates. You only need to configure the binary log format on the databases that you want to connect to Fivetran.
(Optional) Enable GTID mode by setting these additional parameters:
- gtid_mode to
ON - enforce_gtid_consistency to
ON
- gtid_mode to
Configure replica for history mode
If you have connected Fivetran to a read replica and plan to run your connection in history mode, do the following:
Connect to your read replica as a user with
SUPERprivileges.Check your read replica's
slave_parallel_workersvalue.If the
slave_parallel_workersvalue is0, you do not need to any additional configuration.If the
slave_parallel_workersvalue is not0, do the following:Run the following commands to update the
slave_parallel_typeandslave_preserve_commit_ordervalues.SET GLOBAL slave_parallel_type = 'LOGICAL_CLOCK'; SET GLOBAL slave_preserve_commit_order = 1;Next, connect to your primary instance as a user with
SUPERprivileges, then run the following command to set thebinlog_order_commitsto1.SET GLOBAL binlog_order_commits = 1;
Learn more about these variables in MySQL's replica server variables documentation.
Fivetran Teleport Sync
Open a connection to your MySQL primary database using your favorite SQL tool (for example, MySQL Workbench or the
mysqlcommand in your operating system's terminal window).Create a Fivetran user and grant SELECT permissions by running the following SQL commands. Replace
<username>andpasswordwith a username and password of your choice.CREATE USER <username>@'%' IDENTIFIED WITH mysql_native_password BY 'password'; -- Option 1: Grant user SELECT permission on all tables and columns GRANT SELECT ON *.* TO <username>@'%'; -- Option 2: Grant user SELECT permission on only specified table and columns GRANT SELECT ON <tables/columns> TO <username>@'%';
If there are errors when running these commands, you may lack sufficient privileges and should contact your database administrator.
Finish Fivetran configuration
In your connection setup form, enter a Destination schema prefix. This is used as the connection name and cannot be modified once the connection is created.
Depending on your selection in the Destination schema names field, we will either prefix the connection name to each replicated schema or use the source schema names instead.
In the Destination schema names field, choose the naming convention you want Fivetran to use for the schemas, tables, and columns in your destination:
- Source naming: Preserves the original schema, table, and column names from the source system in your destination.
- Fivetran naming: Standardizes the schema, table, and column names in your destination according to the Fivetran naming conventions.
If you want to modify your selection, make sure you do it before you start the initial sync.
Depending on your selection, we will either prefix the connection name to each replicated schema or use the source schema names instead.
(Hybrid Deployment only) If your destination is configured for Hybrid Deployment, the Hybrid Deployment Agent associated with your destination is pre-selected for the connection. To assign a different agent, click Replace agent, select the agent you want to use, and click Use Agent.
(Not applicable to Hybrid Deployment) Choose your Connection method. If you selected Connect via an SSH tunnel, copy or make a note of the Public Key and add it to the
authorized_keysfile while configuring the SSH tunnel, and provide the following information:- SSH hostname (do not use a load balancer's IP address/hostname)
- SSH port
- SSH user
- If you enabled TLS on your database in Step 1, make sure to keep the Require TLS through Tunnel toggle turned ON.
In the Host field, enter your database host's IP (for example,
1.2.3.4) or domain (for example,your.server.com).Enter your database instance's Port number (usually
3306).In the User field, enter
<username>@<servername>, where<servername>is part of your Azure host URL:<servername>.database.windows.net.Enter the Password for the Fivetran-specific user that you created in Step 4.
(Optional for Hybrid Deployment) If you want to use a TLS connection between your Hybrid Deployment Agent and Fivetran cloud, set the Require TLS toggle to ON.
Before you set this toggle to ON, you must first enable TLS on your database. Learn how in the Security section of the MySQL reference manual for your database version.
Under Update Method, choose how Fivetran will detect data changes in your source database:
- Read Changes via Binary Log - Reads directly from the MySQL binary log using Fivetran's Binary log incremental sync method.
- Detect Changes via Fivetran Teleport Sync - Detects changes by comparing source and snapshot data using Fivetran Teleport Sync incremental sync method.
(Binary log only) Enter a unique Replica ID for Fivetran. We provide a random replica ID, but you can provide your own if you'd prefer or if the setup form's replica ID conflicts with one of your existing replica IDs.
(Not applicable to Hybrid Deployment) Copy the Fivetran's IP addresses (or CIDR) that you must safelist in your firewall.
Click Save & Test. Fivetran tests and validates our connection to your Azure Database for MySQL database. Upon successful completion of the setup tests, you can sync your data using Fivetran.
Setup tests
Fivetran performs the following tests to ensure that we can connect to your Azure Database for MySQL database and that it is properly configured:
- The Connecting to SSH Tunnel Test validates the SSH tunnel details you provided in the setup form. It generates a pop-up window where you must verify the SSH fingerprint. It then checks that we can connect to your database using the SSH Tunnel. (We skip this test if you are connecting directly.)
- The Connecting to Host Test verifies that the database host is not private and checks that we can connect to the host.
- The Validating TLS Connection to Source Database Test validates the server certificate and checks that we can connect to your database using TLS. An untrusted certificate generates a pop-up window where you must choose which certificate you want Fivetran to use. (We skip this test if you selected an indirect connection method and then disabled the Require TLS through Tunnel toggle.)
- The Validating Database User Test validates the database credentials you provided in the setup form.
- (Binary log only) The Checking Database Configuration Test verifies that we can find your database's server ID. It then checks your binary log configuration and confirms that we can connect to the binary log.
- The Validating Database Type Test checks that your database type matches the connector type. For example, this test will fail if you try to set up an Azure Database for MySQL connection with a Amazon RDS for MySQL database. To perform this test, the Fivetran user needs permission to access the
mysqlsystem database, though we do not sync any data from that DB.
The tests may take a few minutes to finish running.