Configuring Encrypted Network Connection
This section describes the steps required to set up a secure HVR network connection between an HVR Hub and a remote location using:
- the default private key and public certificate files which are delivered with HVR in $HVR_HOME/lib/cert (Standard Configuration Steps)
- a newly generated private key and public certificate (Advanced Configuration Steps)
Only the public certificate should be stored on a hub machine, whereas on a remote location, both the public certificate and the private key should be present.
Standard Configuration Steps
The steps in this section are to set up a secure HVR connection using the default private key and public certificate provided by HVR. The example here assumes that a channel and remote locations are already created and configured.
In case the connection to a remote HVR location is not configured, see the appropriate section Configuring Remote Installation of HVR on Unix or Linux or Configuring Remote Installation of HVR on Windows.
Set up HVR on the remote HVR location to expect an encrypted connection.
Steps for Unix/Linux
Depending on the daemon type available, one of the following configuration methods can be used:
HVR on the remote machine consists of an HVR executable file with option –r which is configured to listen on a specific port number. Option –Kpair should be added to specify the public certificate and private key respectively. The default basename for the public certificate and private key pair is hvr. For more information about options -r and -K, refer to the respective sections of the Hvr command page.
For systemd, add option -Khvr to the following line into file in /etc/systemd/system/hvr@.service:
ExecStart=/home/hvruser/hvr/hvr_home/bin/hvr -r -KhvrFor xinetd, add option -Khvr to the following line in file /etc/xinetd.d/hvr:
server_args = -r -Khvr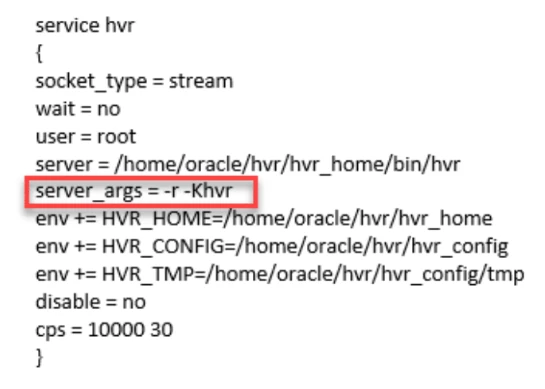
For inetd, add option -Khvr to the following line in file /etc/inetd.conf:
hvr stream tcp nowait root /usr/hvr/hvr_home/bin/hvr hvr -r -Khvr -EHVR_HOME=/usr/hvr/hvr_home -EHVR_CONFIG=/usr/hvr/hvr_config -EHVR_TMP=/tmp
Start HVR Remote Listener using the following command:
hvrremotelistener -N -d -Khvr 4343
Steps for Windows
Create and run HVR Remote Listener service that requires SSL encryption for incoming connections.
In the HVR GUI on the remote machine, click File in the main menu and select HVR Remote Listener.
If the HVR Remote Listener is already running, click Stop and then Destroy so that a new one with SSL encryption can be created.
In the HVR Remote Listener dialog, click Create.
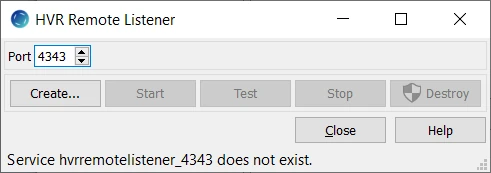
In the Create Windows Service dialog, select Require SSL on incoming connections and specify the basename of the Local Certificate Key Pair. The default basename for the public certificate and private key pair is hvr.
Click Create.
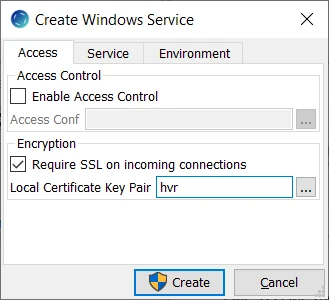
Click Start to start the service.
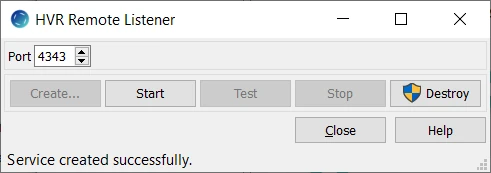
In the Windows Services, you will see a service called HVR Remote Listener on port 4343 created and running.
Define action LocationProperties /SslRemoteCertificate to register the public certificate file in the channel configuration.
Right-click the channel, navigate to New Action and click LocationProperties.
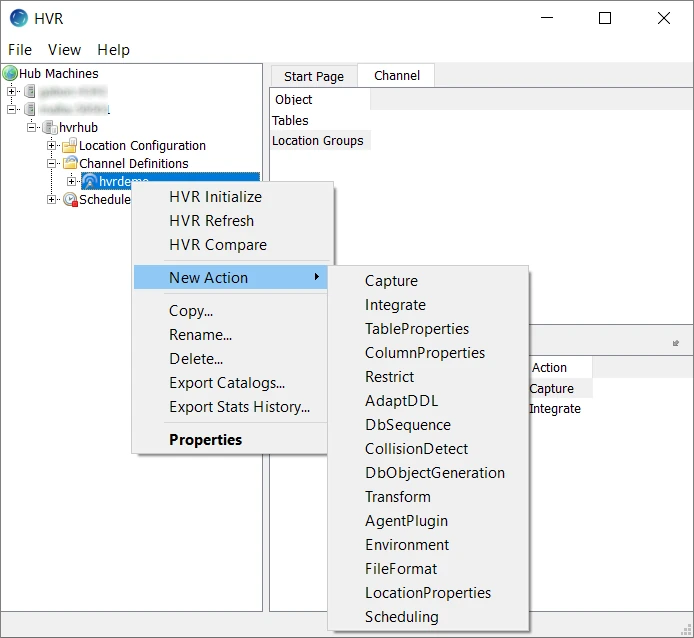
In the New Action: LocationProperties dialog, select SSLRemoteCertificate and specify the basename of the Local Certificate Key Pair. The default basename for the public certificate and private key pair is hvr.
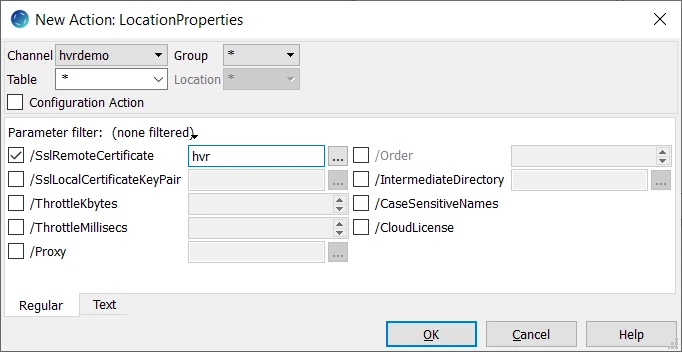
Execute HVR Initialize for this action to take effect. Right-click the channel and select HVR Initialize. Ensure the Scripts and Jobs option is selected and click Initialize.
This (hvrinit) can also be executed on the command line as follows:
hvrinit -oj hubdb hvrdemo
Advanced Configuration Steps
The steps in this section are to set up a secure HVR connection using a newly generated private key and public certificate.
There are two methods how the encrypted connection can be configured in an HVR channel:
- Use different certificate key pair on source and target machines. Example: MyCertificate1 and MyCertificate2. For this method, copy the public certificate files on source (MyCertificate1) and target (MyCertificate2) to the hub machine. Define two separate actions LocationProperty /SslRemoteCertificate for source and target groups in the channel.
- Use same certificate key pair on source and target machines. Example: MyCertificate. For this method, the certificate key pair should be copied to the other remote location also. For example, if the certificate key pair was generated on the source machine, then it should be copied to the target machine also and the public certificate should be copied to the hub machine. Define one action LocationProperty /SslRemoteCertificate in the channel.
The example here assumes that a channel and remote source location are already created and configured.
In case the connection to a remote HVR location is not configured, see the appropriate section Configuring Remote Installation of HVR on Unix or Linux or Configuring Remote Installation of HVR on Windows.
On a remote location, generate a new private key and public certificate pair using command Hvrsslgen. For more information on the arguments and various options available for this command, refer to section Hvrsslgen.
Copy the public certificate file into the $HVR_HOME/lib/cert directory of the hub machine.
Set up HVR on the remote HVR location to expect an encrypted connection (using the newly generated public certificate and private key pair):
Steps for Unix/Linux
Depending on the daemon type available, one of the following configuration methods can be used:
HVR on the remote machine consists of an HVR executable file with option –r which is configured to listen on a specific port number. Option –Kpair should be added to specify the public certificate and private key respectively. In this example, the basename for the public certificate and private key pair is MyCertificate. For more information about options -r and -K, refer to the respective sections of the Hvr command page.
For systemd, add option -K to the following line into file in /etc/systemd/system/hvr@.service:
ExecStart=/home/hvruser/hvr/hvr_home/bin/hvr -r StandardInput=socket KillMode=process -KMyCertificateFor xinetd, add option -K to the following line in file /etc/xinetd.d/hvr:
server_args = -r -KMyCertificateFor inetd, edit file /etc/inetd.conf:
hvr stream tcp nowait root /usr/hvr/hvr_home/bin/hvr hvr -r -EHVR_HOME=/usr/hvr/hvr_home -EHVR_CONFIG=/usr/hvr/hvr_config -EHVR_TMP=/tmp -KMyCertificate
Start HVR Remote Listener using the following command:
hvrremotelistener -N -d -KMyCertificate 4343
Steps for Windows
Create and run HVR Remote Listener service that requires SSL encryption for incoming connections.
In the HVR GUI on the remote machine, click File in the main menu and select HVR Remote Listener.
If the HVR Remote Listener is already running, click Stop and then Destroy so that a new one with SSL encryption can be created.
In the HVR Remote Listener dialog, click Create.

In the Create Windows Service dialog, select Require SSL on incoming connections and specify the name for the Local Certificate Key Pair, e.g. 'MyCertificate'.
Click Create.
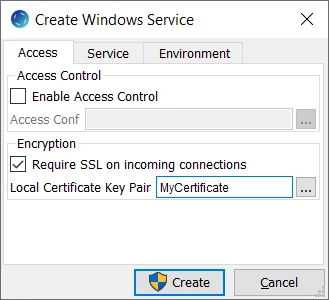
Click Start to start the service.

In the Windows Services, you will see a service called HVR Remote Listener on port 4343 created and running.
Define action LocationProperties /SslRemoteCertificate to register the public certificate file in the channel configuration.
Right-click the location group, navigate to New Action and click LocationProperties.
In the New Action: LocationProperties dialog, select SSLRemoteCertificate.
Browse and select the public certificate file (MyCertificate.pub_cert).
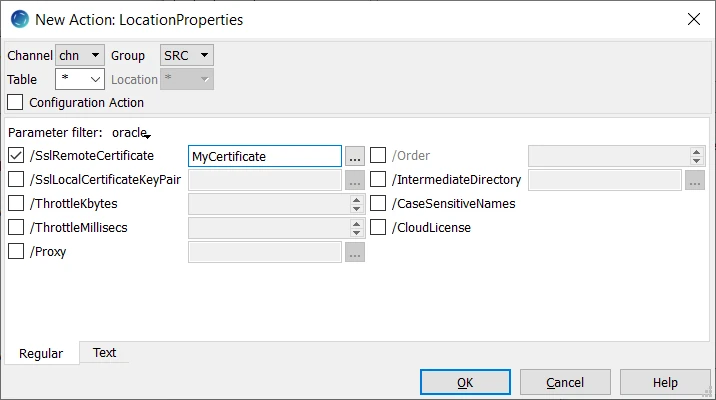
Execute HVR Initialize for this action to take effect. Right-click the channel and select HVR Initialize. Ensure the Scripts and Jobs option is selected and click Initialize.

This (hvrinit) can also be executed on the command line as follows:
hvrinit -oj hubdb mychn