Azure Service Bus Setup Guide
Follow our setup guide to connect Azure Service Bus to Fivetran.
Prerequisites
To connect Azure Service Bus to Fivetran, you need an Azure account with a Service Bus namespace.
For more information, see Microsoft's Service Bus namespace documentation.
Setup instructions
Select connection method
The Connection Method option is only available for Business Critical accounts.
First, decide whether to connect Fivetran to your Azure Service Bus instance directly, using an SSH tunnel, or using Azure Private Link.
Connect directly
Fivetran connects directly to your Azure Service Bus instance. This is the simplest connection method.
To connect directly, create a firewall rule to allow access to Fivetran's IPs.
Connect using SSH (TLS optional)
Fivetran connects to a separate server in your network that provides an SSH tunnel to your Azure Service Bus instance. You must connect through SSH if your instance is in an inaccessible subnet on a virtual network.
To connect using SSH, create a firewall rule to allow access to your SSH tunnel server's IP address.
Before you proceed to the next step, you must follow our SSH connection instructions to give Fivetran access to your SSH tunnel. If you want Fivetran to tunnel SSH over TLS, follow Azure's TLS setup instructions to enforce a minimum TLS required version on your namespace.
Connect using Azure Private Link
You must have a Business Critical plan to use Azure Private Link.
Azure Private Link allows Virtual Networks (VNets) and Azure-hosted or on-premises services to communicate with one another without exposing traffic to the public internet. Learn more in Microsoft's Azure Private Link documentation.
Follow our Azure Private Link setup guide to configure Private Link for your service bus.
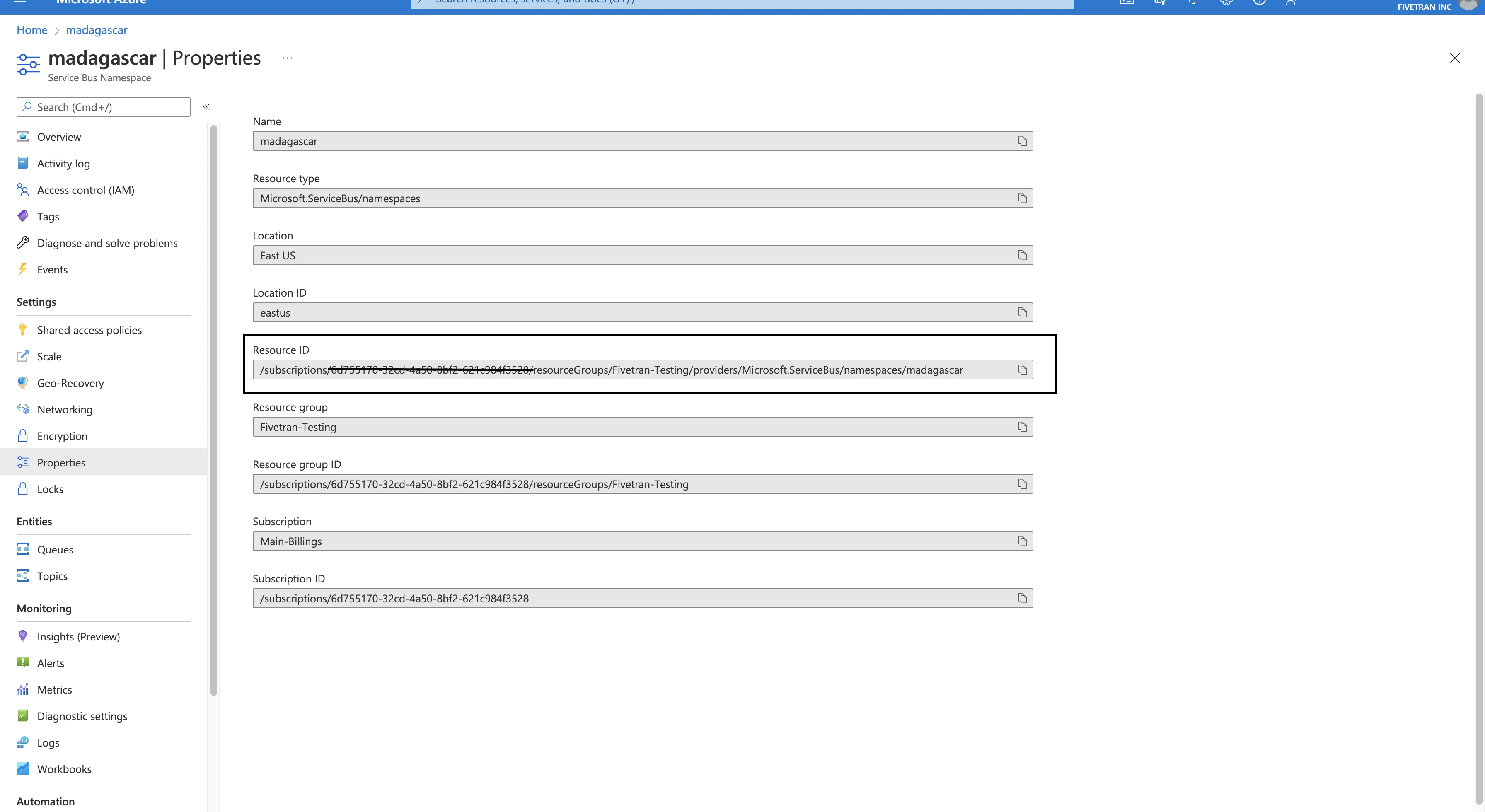
If you want to connect to Fivetran through Azure Private Link, contact Fivetran Support for help. Provide your namespace's Resource ID in your message so we can set up your private endpoint.
Select authentication method
Select whether you want to authenticate using Connection String or Microsoft Entra ID (formerly Azure Active Directory).
Connection String
Open the Azure Service Bus service.
Open the Service Bus namespace for which you want to create the connection.
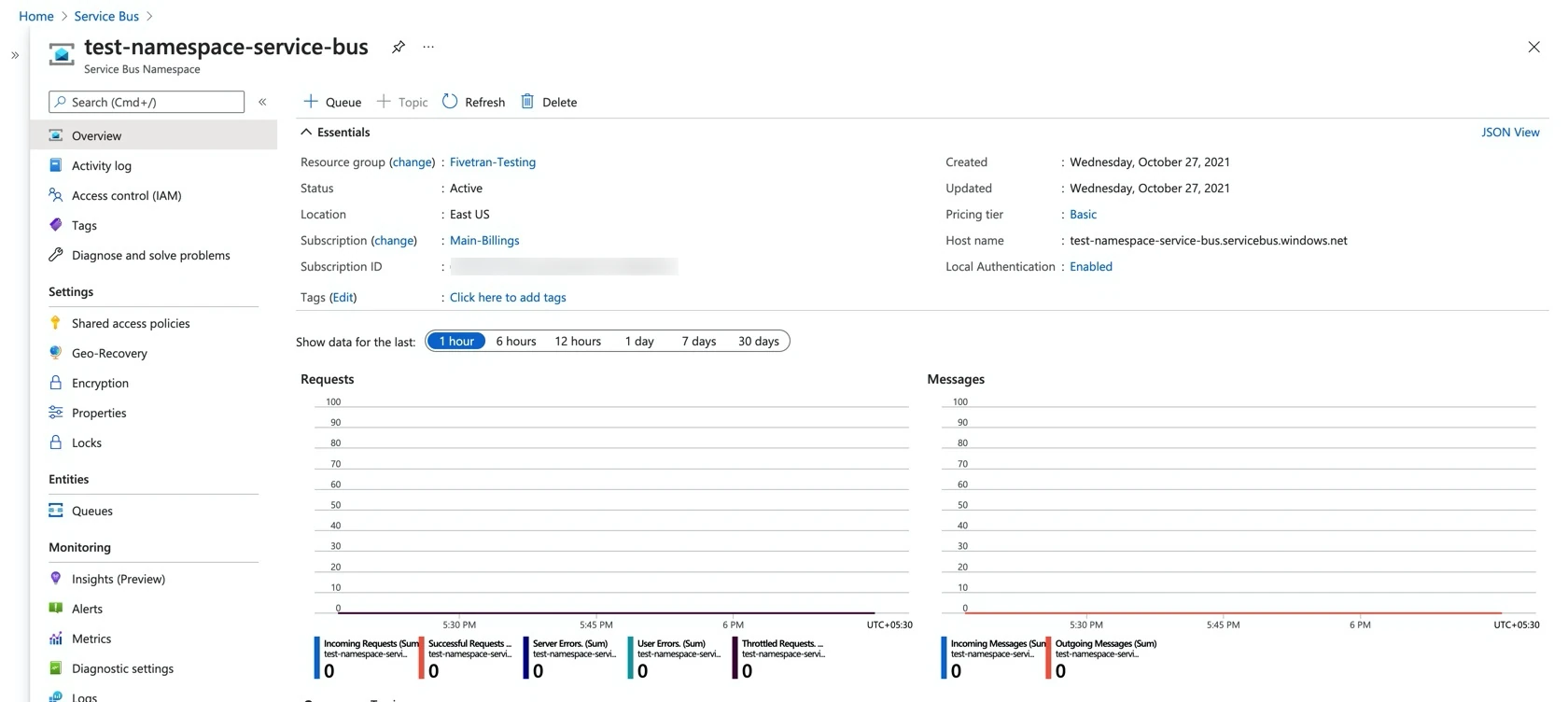
Go to Settings > Shared access policies.
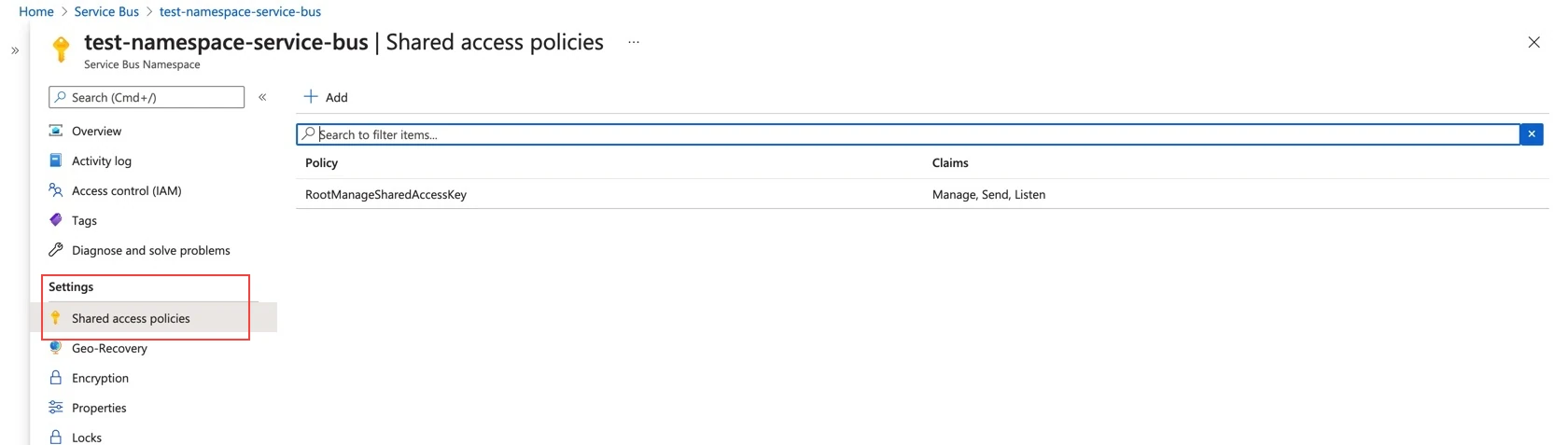
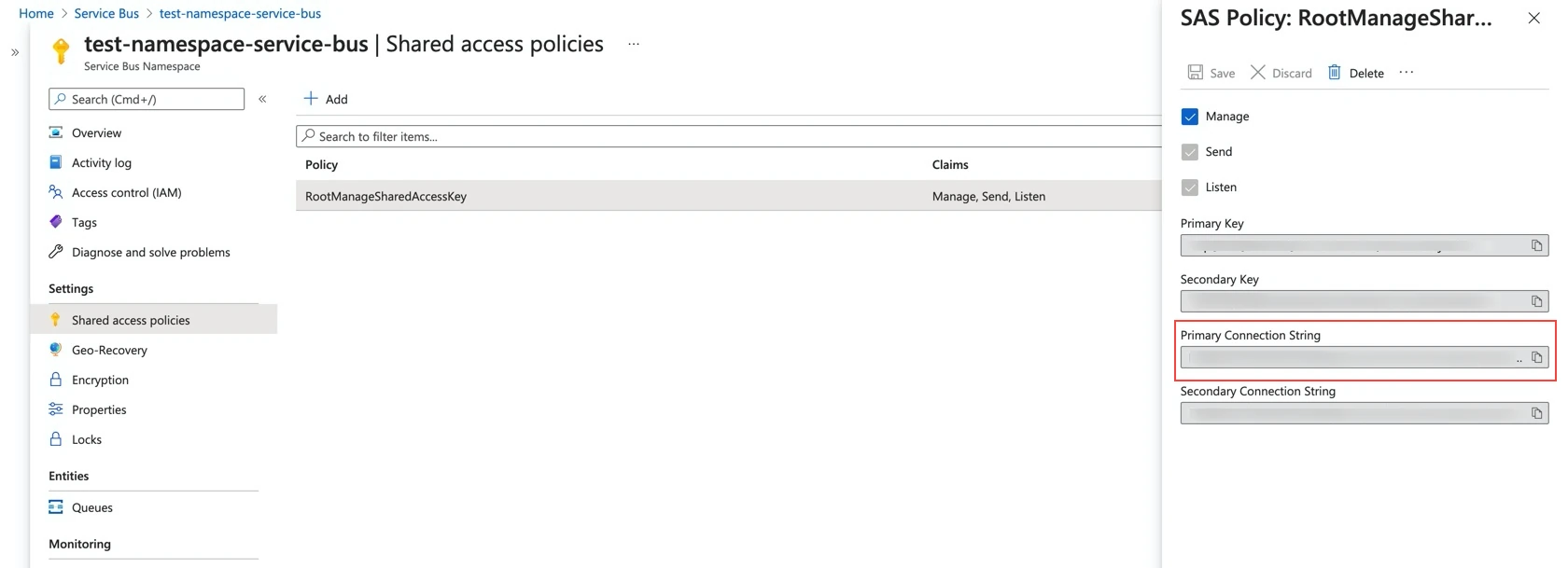
Select a shared access key with the Manage, Send, and Listen scopes.
If you don't have a shared access key, create one.
Make a note of the Primary Connection String. You will need it to configure Fivetran.
Microsoft Entra ID
Add role assignment
Log in to your Azure portal and go to Azure Service Bus homepage.
Click Access control (IAM) and then click Add.
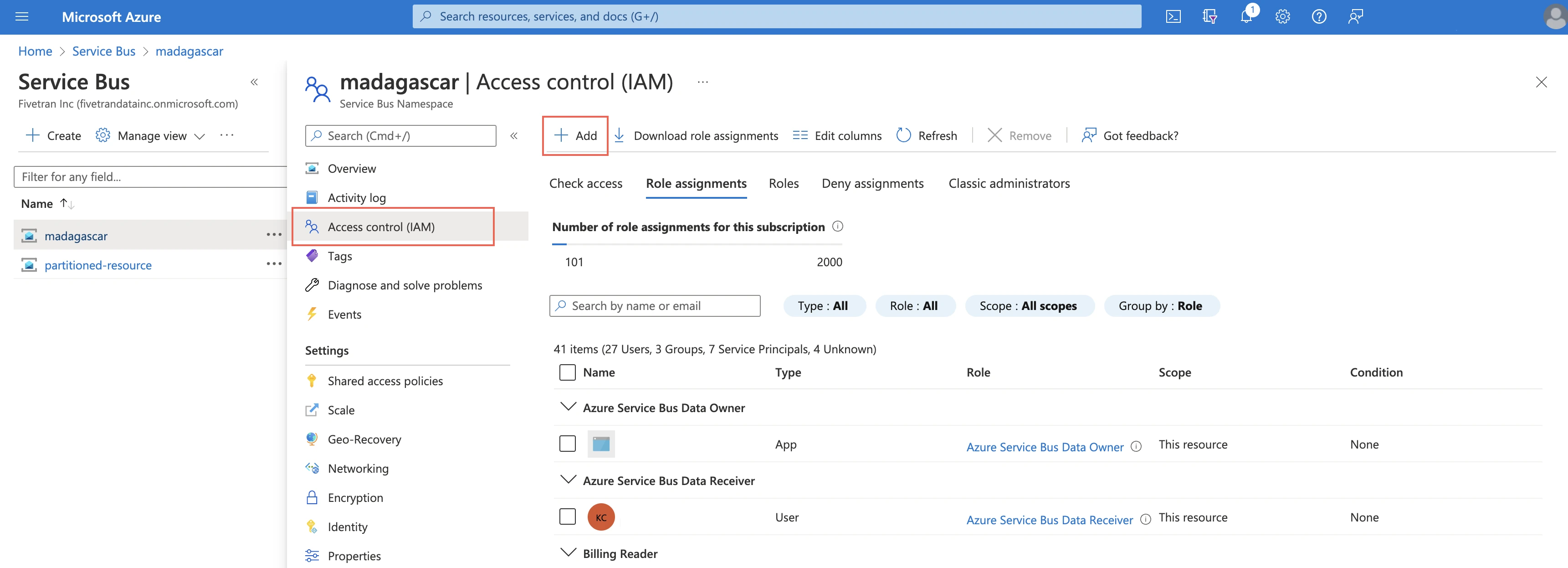
Select Azure Service Bus Data Receiver.
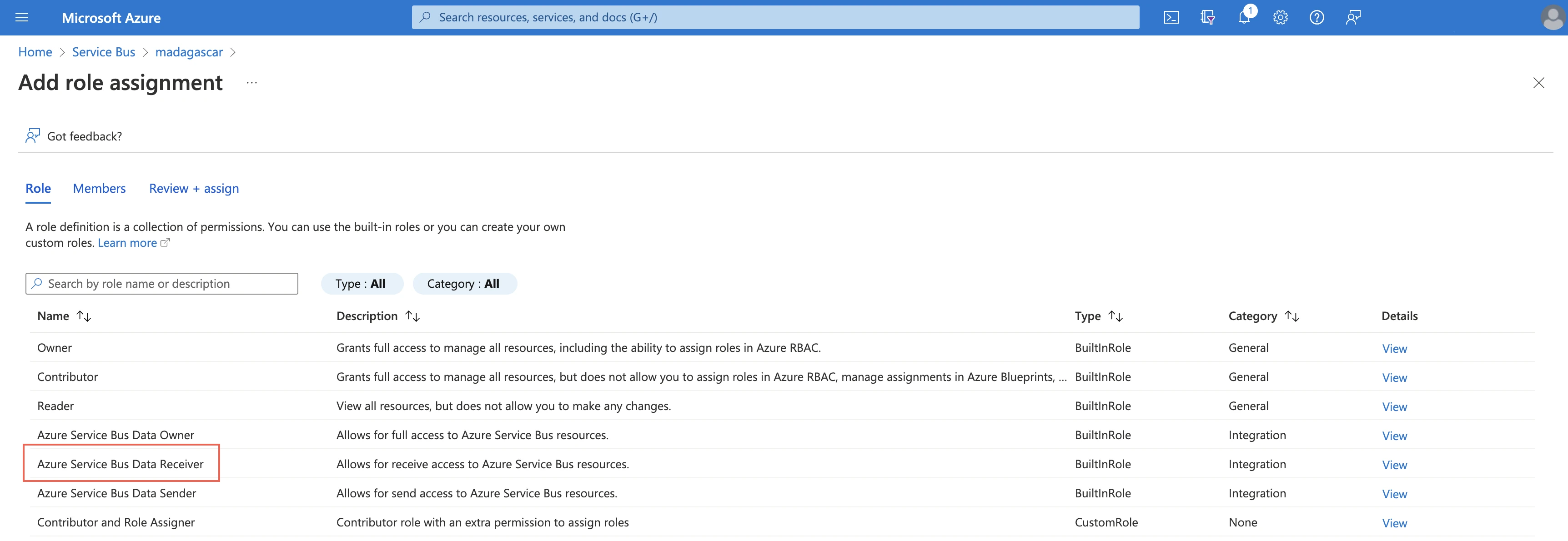
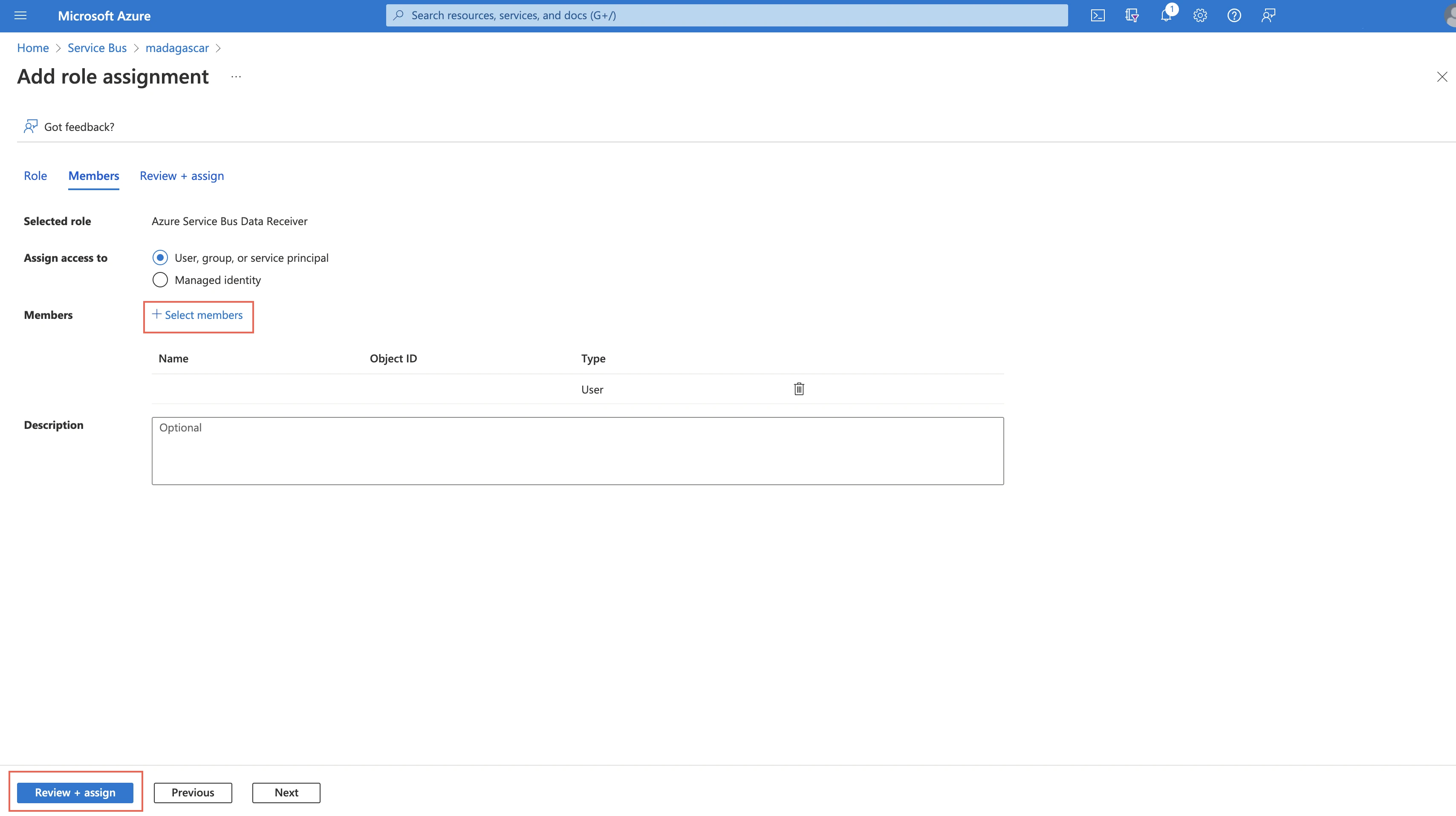
Click +Select members and add the member you want to assign.
Click Review+Assign.
Authorize Fivetran
- In the connection setup form, click Authorize. You will be redirected to your Microsoft login account to authorize Fivetran's access.
- Log in to your Azure account which has the Azure Service Bus Data Receiver role.
- Click Accept to authorize Fivetran's read access to your service bus data. Once you have finished, you will be redirected back to Fivetran.
Finish Fivetran configuration
In the connection setup form, enter the Destination schema name of your choice.
Select the Authentication Method you want to use:
- If you choose Connection String, enter the Connection String you found in Step 2.
- If you choose Microsoft Entra ID, enter the Namespace of your Service Bus.
Select your message type: Json, Avro, Text, or Xml.
If you choose Json, select a sync type: Packed or Unpacked.
If you choose Avro, enter the following schema registry credentials:
- Schema Registry URLs
- Schema Registry Key
- Schema Registry Secret
(Optional) Set the Enable Advanced Options toggle to ON.
The Enable Advanced Options toggle option is only available for Business Critical accounts.
Select your Connection Method: Direct, or Connect via Private Link, or Connect via SSH Tunnel
- If you chose Connect via Private Link, see Connect using Azure Private Link.
- If you chose Connect via SSH Tunnel, do the following:
- Enter the SSH tunnel machine's IP address
- Enter the user name
- Copy the public key from the connection setup form and paste it into the
.ssh/authorized_keysfile inside the home folder on the tunnel machine
If you do not have manage permissions for your namespace, toggle the hasManagePermissions to OFF. To sync data without manage permissions, do the following:
- Enter the topics which you want to sync
- Create the subscription and enter the name of the subscription that Fivetran can use to query the data
Click Save & Test. Fivetran will take it from here and sync your Azure Service Bus data.
If you have manage permissions, Fivetran creates a Service Bus subscription for every connection with the name format
fivetran_sub_<schema>in your Azure namespace for each topic. If you don't have manage permissions, Fivetran creates a Service Bus subscription for every connection with the name formatfivetran_sub_<schema>in your Azure namespace.
Fivetran tests and validates the Azure Service Bus connection. On successful completion of the setup tests, you can sync your Azure Service Bus data to your destination.
Setup tests
Fivetran performs the following Azure Service Bus connection tests:
The Connectivity test validates your Azure Service Bus credentials and checks if Fivetran is able to connect to Azure Service Bus via Private Link. We perform this test only if you select Connect via Private link as the Connection Method.
The Subscriber/Topic test performs one of the following actions:
- If the Do you have manage permissions? toggle is ON, Fivetran checks whether the connection can create a subscriber and fetch a message from each topic in the namespace.
- If the Do you have manage permissions? toggle is OFF, Fivetran uses an existing subscriber client to check if we can fetch a message from each topic in the namespace.