Mutual Authentication (mTLS)
You can use our Mutual Authentication mode, which incorporates Mutual TLS (mTLS), to enhance the security of your AMQP connector. This added layer of security ensures a 2-way authentication process, where both broker and Fivetran verify each other’s identities before any data exchange occurs. During the connection setup, both broker and Fivetran exchange and validate each other's certificates, ensuring a secure and trusted communication channel.
Setup instructions for Solace broker
Create an Internal Certificate Authority (CA)
Use OpenSSL to create an internal CA if your organization doesn't already have one.
Generate a Private Key and CA Certificate
Run the following command to generate a private key and CA certificate:
openssl req -newkey rsa:2048 -nodes -keyout MyRootCaKey.key \
-x509 -days 365 -out MyRootCaCert.pem \
-subj "/C=GB/ST=London/L=London/O=Global Security/OU=IT Department/CN=*.messaging.solace.cloud"
This command generates:
MyRootCaKey.key— the private key for your internal CA. Keep this file secure.MyRootCaCert.pem— the public CA certificate. You can distribute this to clients or upload it to your event broker if needed.
Create and sign a client certificate
Create a private key and certificate for your connector.
Generate the client private key
Run the following command to generate the client private key:
openssl genrsa -out client1.key 2048
Create a certificate signing request
Run the following command to create a Certificate Signing Request (CSR):
openssl req -new -key client1.key -out MyClient1.csr \
-subj "/C=GB/ST=London/L=London/O=Global Security/OU=IT Department/CN=client1.messaging.solace.cloud"
Sign the client certificate with the internal CA
Run the following command to sign the client certificate:
openssl x509 -req -in MyClient1.csr -CA MyRootCaCert.pem -CAkey MyRootCaKey.key \
-CAcreateserial -out clientCert1.pem -days 365 -sha256
You now have:
client1.key— client's private keyclientCert1.pem— client's signed certificate
Our AMQP connection requires these two files.
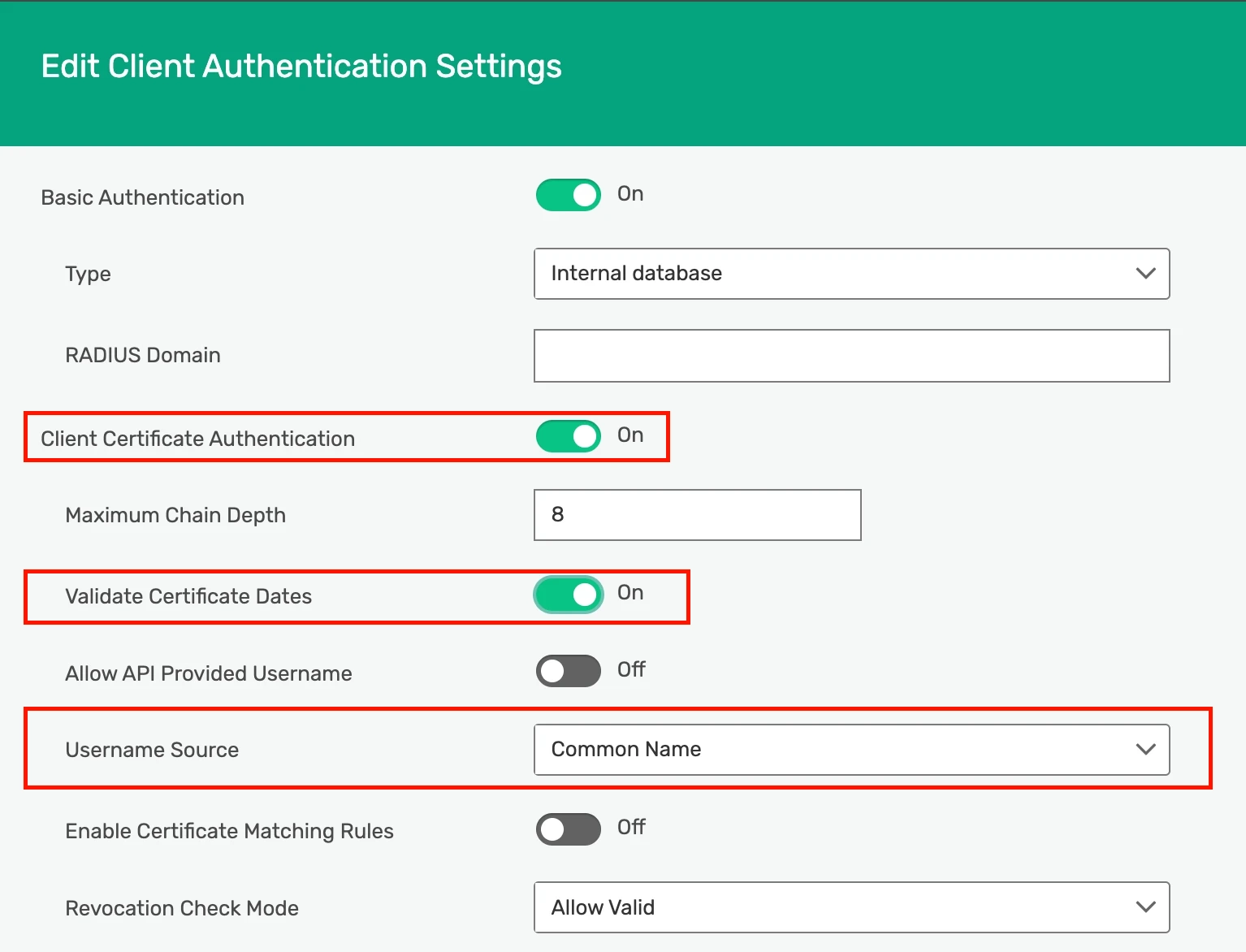
Configure client certificate authentication in the event broker
In PubSub+ Cloud Console, go to Cluster Manager -> Service Details -> Manage -> Authentication and Security.
In Service Authentication, click Open Broker Manager.
Enable Client Certificate Authentication and Validate Certificate Dates to ensure certificates are not expired.
In the Username Source drop-down menu, select Common Name (CN).
This ensures the client's username will be fetched automatically from the CN in the certificate, for example,
client1.messaging.solace.cloud).Apply and save your settings.
Upload internal CA certificate to the event broker
In Authentication and Security, go to the Certificate Authorities tab.
Click Add Client Certificate Authority.
Enter a name (no spaces or special characters).
Open your
MyRootCaCert.pemfile and copy its contents including:-----BEGIN CERTIFICATE----- ...contents... -----END CERTIFICATE-----Paste it into the Domain Certificate Content field and click Save.
(Optional) Add client username
By default, the broker uses the Common Name (CN) from the certificate as the client username. For example, if your client certificate CN is client1.messaging.solace.cloud, that becomes the username.
If you need to verify:
Open PubSub+ Broker Manager.
Go to Access Control → Client Usernames.
Confirm that the username (CN) exists and is enabled.
The server certificate used by the event broker should be issued by a public CA, so you do not need to provide any CA certificate while creating the connector. You only need to provide your client certificate and private key generated by your internal CA.
Finish Fivetran configuration
- Go back to the Fivetran AMQP connection setup form.
- In the connection setup form, select Mutual TLS as the Authentication Method.
- Complete the connection setup.