Splunk Logging Setup Guide
Follow our step-by-step guide to integrate Fivetran logs into your Splunk monitoring system.
Follow this setup guide to send data about your Fivetran connections to Splunk. To sync data from Splunk to your destination, use our Splunk connector.
Prerequisites
To connect Splunk to Fivetran, you need:
- A Splunk account
- The
edit_token_httppermission to enable HTTP Event Collector (HEC)
We support HEC on Splunk Enterprise platforms, including cloud and on-premise instances, and Splunk Cloud deployments.
In Splunk
This step-by-step guide explains how to configure HEC on Splunk Enterprise. To learn how to do that on Splunk Cloud, refer to Splunk Documentation.
Enable HTTP Event Collector
Set up your HTTP Event Collector to configure a secret token that Fivetran can use to send data using HTTP and HTTPS.
Click Settings > Data Inputs.
Click HTTP Event Collector.
Click Global Settings.
Set the All Tokens toggle to Enabled.
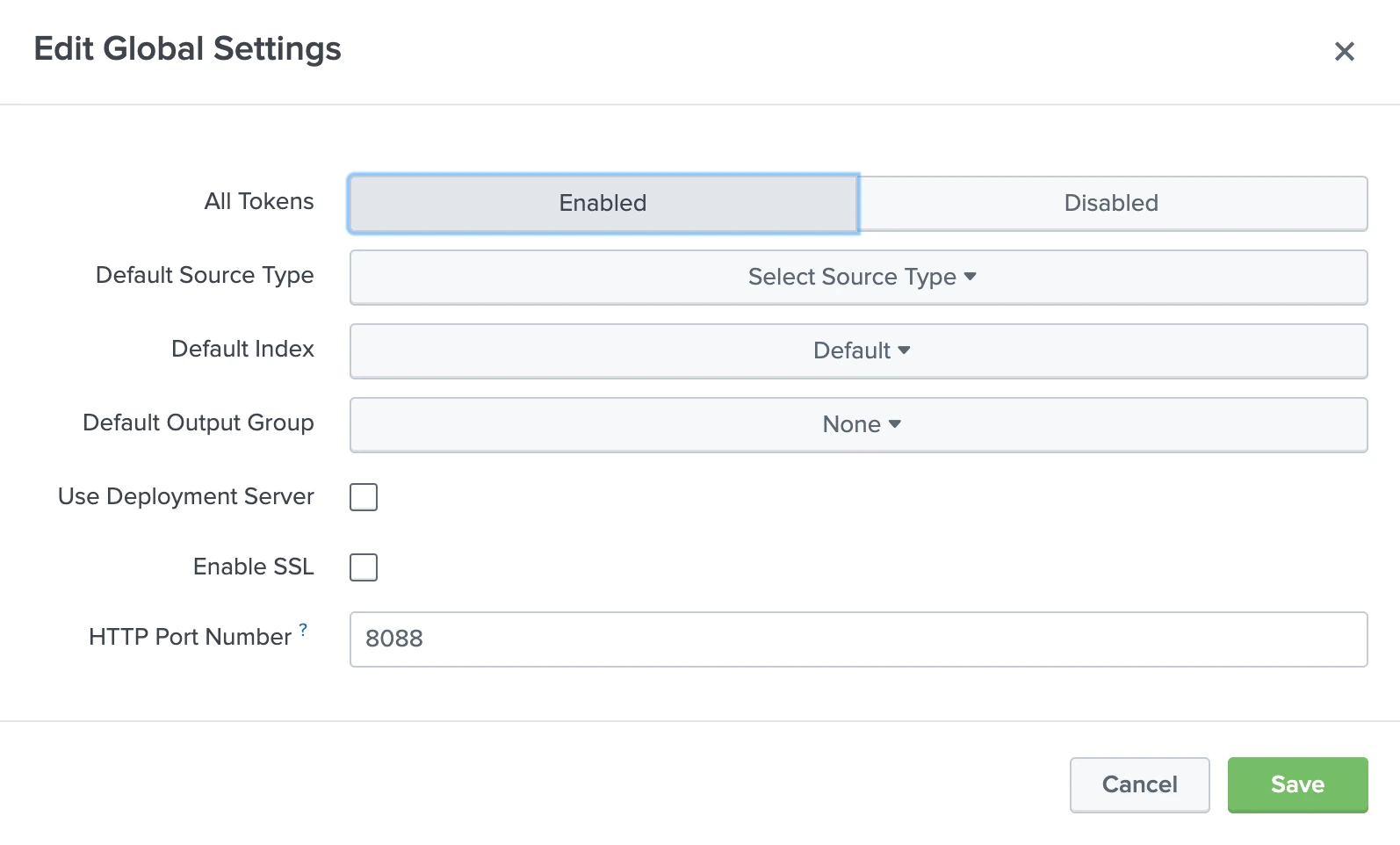
(Optional) Select a Default Source Type for all HEC tokens.
(Optional) Select a Default Index.
(Optional) Select a Default Output Group.
(Optional) Select the Use Deployment Server checkbox to use a deployment server to handle configurations for HEC tokens.
(Optional) Select the Enable SSL checkbox to have HEC listen and communicate over HTTPS rather than HTTP.
(Optional) Enter a number in the HTTP Port Number field for HEC to listen on. Make a note of the port number. You will need it to configure Fivetran.
Confirm that your firewall rules don’t block incoming and outgoing traffic through the port number.
Click Save.
Make a note of the Splunk instance that runs HEC. This is the Host you will need to configure Fivetran.
Create Event Collector Token
Configure a token to use HTTP Event Collector (HEC).
- Click Settings > Add Data.
- Click monitor.
- Click HTTP Event Collector.
- Enter a name for the token in the Name field. For example, Fivetran Logs.
- (Optional) In the Description field, enter a description for the input and click Next.
- (Optional) Confirm the source type and the index for HEC events.
- Click Review.
- Confirm that all settings are correct for the endpoint.
- Click Submit.
- Make a note of the secret token. You will need it to configure Fivetran.
(Optional) Create a Channel Identifier
If you have enabled indexer acknowledgement for the token you generated in Step 2, you must create a channel identifier which is unique (globally unique identifier). For more details about channel identifiers, see Splunk's documentation.
In Fivetran
Go to the external log setup form.
Enter the Port and Host you found in Step 1.
Set the Enable SSL toggle to Enabled.
Enter the Secret Token you configured in Step 2.
(Optional) Enter the Splunk Channel Identifier you created in Step 3.
Click Save & Test. Fivetran will take it from here and sync your logs to Splunk.
Setup test
Fivetran performs the Connect to Splunk HEC setup test to check service accessibility and the credentials you provided in the setup form.